Injection Vulnerability | Owasp juicy shop
Introduction: This is the official companion guide to the OWASP Juice Shop application. Being a web application with a vast number of intended security vulnerabilities, the OWASP Juice Shop is supposed to be the opposite of a best practice or template application for web developers: It is an awareness, training, demonstration and exercise tool for security risks in modern web applications.
Juice Shop is a large application so we will not be covering every topic from the top 10. in this blog we will cover only injection vulnerability.
Types of Injection:
- Code Injection
- SQL Injection
- Command Injection
- Cross Site Scripting
- XPath Injection
- CRLF Injection
- Host Header Injection
- LDAP Injection
- XXE Injection
SQL Injection
SQL Injection is when an attacker enters a malicious or malformed query to either retrieve or tamper data from a database. And in some cases, log into accounts.
In the OWASP JUICY SHOP we have to account as admin account and Blender account
Let’s test the admin account !
1. Admin Account
I typed the password and email as f and ff respectively. click on submit and capture the request in burpsuite.
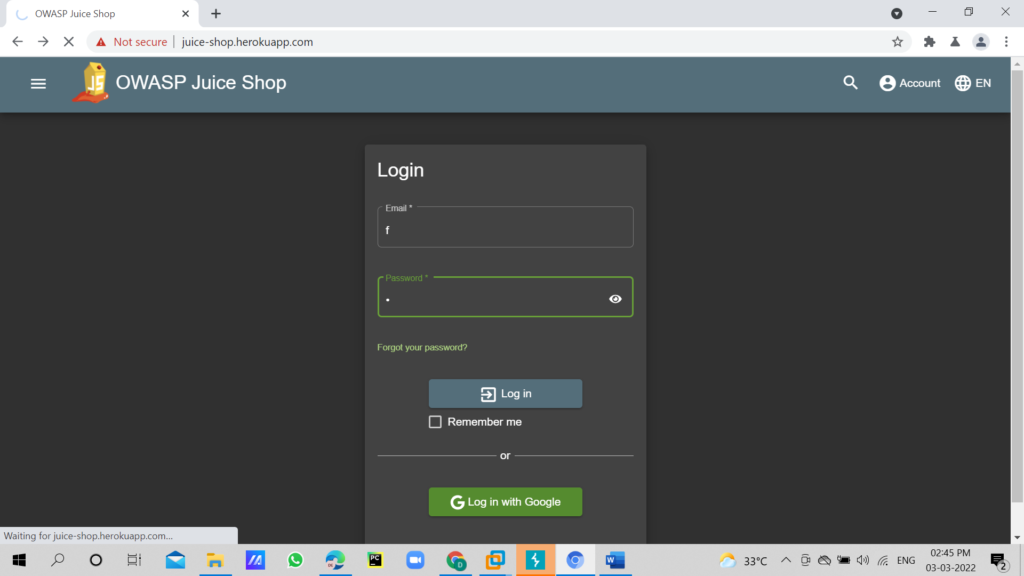
As you can see in below image, we captured the request in burpsuite
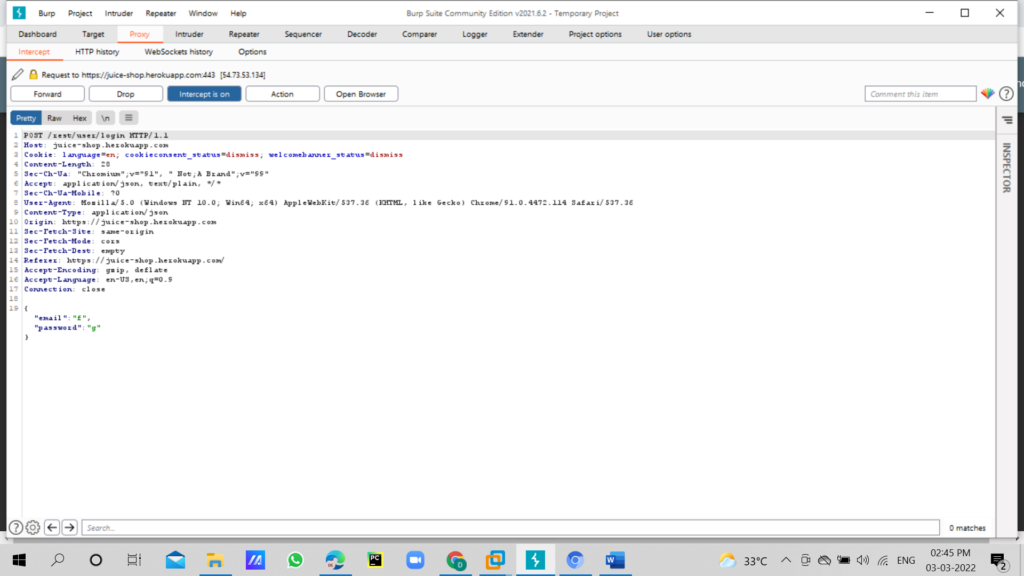
In the burpsuite right click and click on send to repeater tab here we need to test the parameter
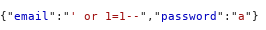
We will now change the email and password parameter use payload next to the email: ‘ or 1=1– and password any random value “a” send the request to server.
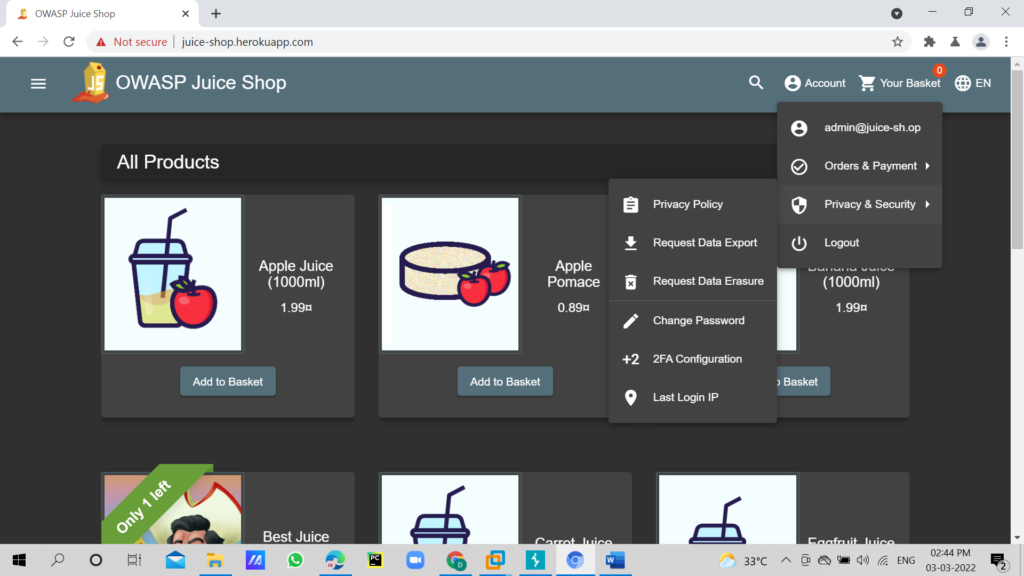
Now right click on request click on show in browser copy the link and paste in browser and it worked.We can check whether admin login is success or not by checking the account in right side corner
How does it work?
- The character ‘ will close the brackets in the SQL query
- ‘OR’ in a SQL statement will return true if either side of it is true. As 1=1 is always true, the whole statement is true. Thus it will tell the server that the email is valid, and log us into user id 0, which happens to be the administrator account.
- The — character is used in SQL to comment out data, any restrictions on the login will no longer work as they are interpreted as a comment. This is like the # and // comment in python and javascript respectively.
2. BLENDER ACCOUNT:
Now here i’m going to login with blender account for that i’m going to use sql payload to bypass the authentication
Open the Blender account and in email, type [email protected] and type random value in password, capture the request in the Burp suite.
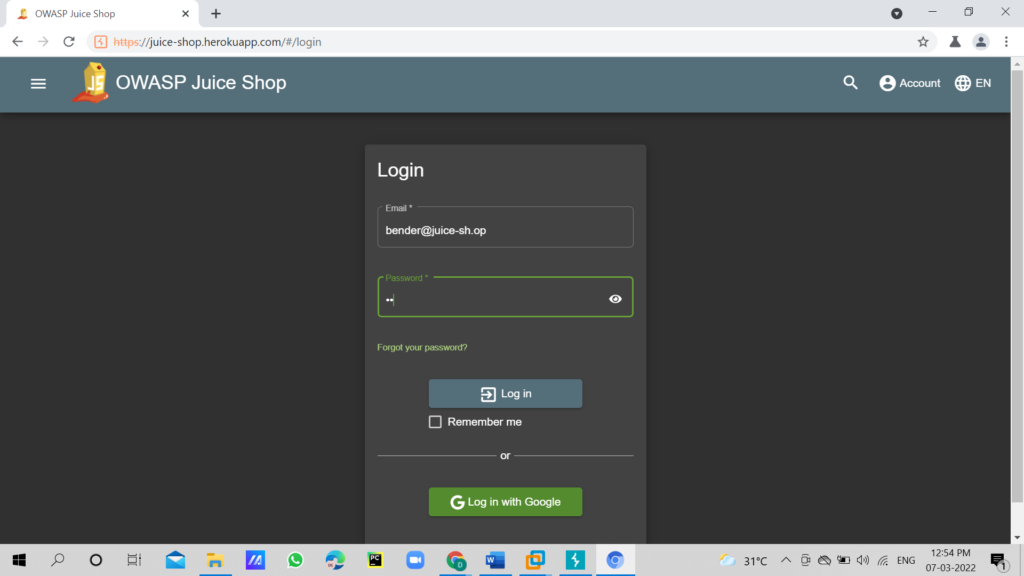
In the burp suite right click and send request to repeater tab, Now we will change the email and password parameter
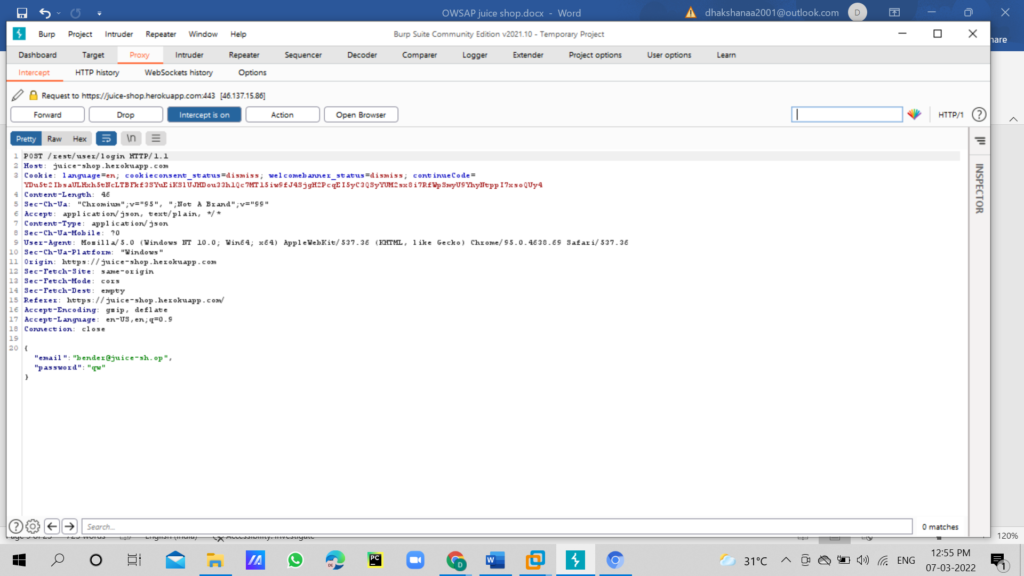
Use SQL payload next to the email: but this time we will put: [email protected]’–as the email. and password any random value “a” and send the request to server.

But why don’t we put the 1=1?
Well, as the email address is valid (which will return true), we do not need to force it to be true. Thus we are able to use ‘– to bypass the login system.
Note the 1=1 can be used when the email or username is not known or invalid.
To confirm login, right click and click on show response in browser click on copy and paste it in same browser.

Author: Dhakshana E is a passionate Cybersecurity Intern, contact LinkedIn