Owasp Juicy Shop | Sensitive Data Exposure
Sensitive Data Exposure: Sensitive Data Exposure vulnerabilities can occur when a web application does not adequately protect sensitive information from being disclosed to attackers. This can include information such as credit card data, medical history, session tokens, or other authentication credentials. It is often said that the most common flaw is failing to encrypt data. One example of this vulnerability is the clear text submission of a password. This is one of many vulnerabilities detected by Burp Scanner. ~ Portswigger
In this blog we are going to use owasp juicy shop vulnerable portal for the demonstration
Access The Confidential Document
Open the owasp Juicy shop site, go to left side corner click on three lines and click on about us option
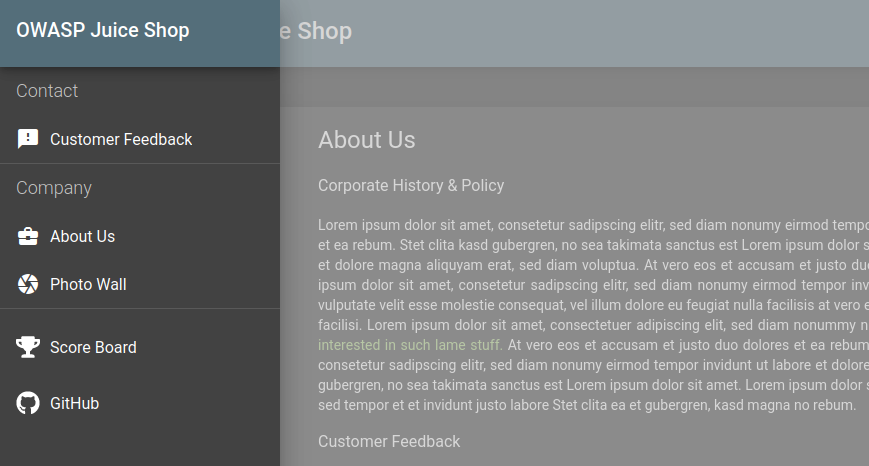
In the above image, I clicked on about us and it show me a paragraph where I can find some different color link in the paragraph. I clicked on it and Immediately a popup comes to download legal.md file, if you want to save you can save otherwise you can leave it. I didn’t save this file
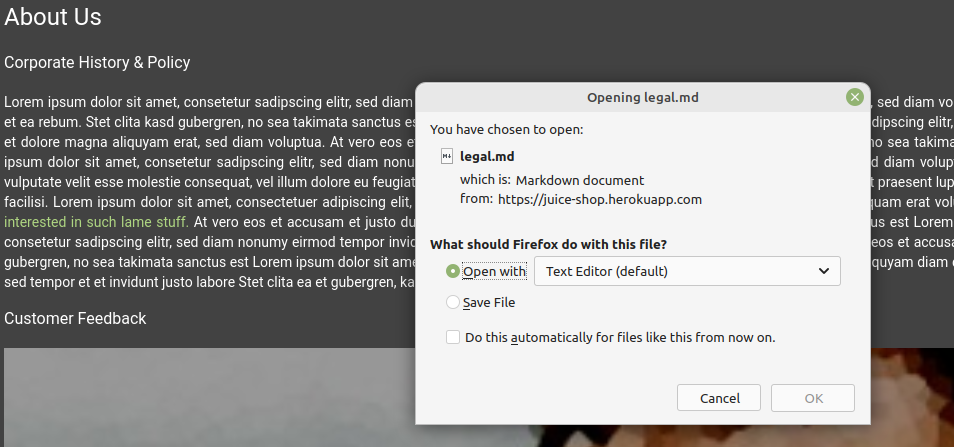
After some time I can find some ftp link is seen in the corner when i keep my mouse in link it shows me site/ftp/legal.md file. What I did is I checked whether ftp is opening or not but luckily it was opening .
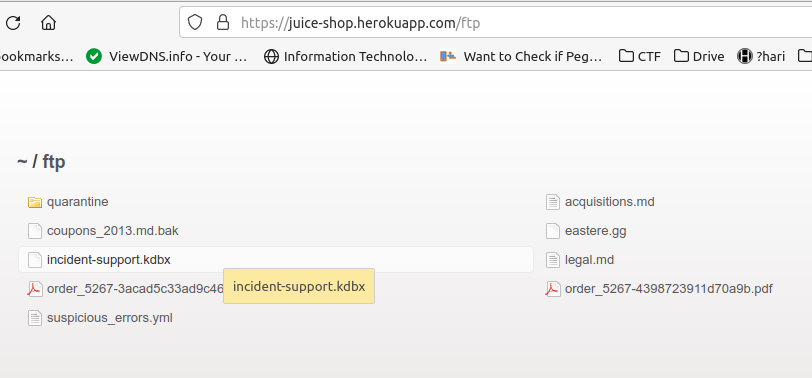
I download the acquisitions file and using Kali Linux I create a directory in desktop named juice shop I moved the acquisitions file from downloads to desktop
Now we can see here the company confidential file and it exposing some company plains
Download the backup file
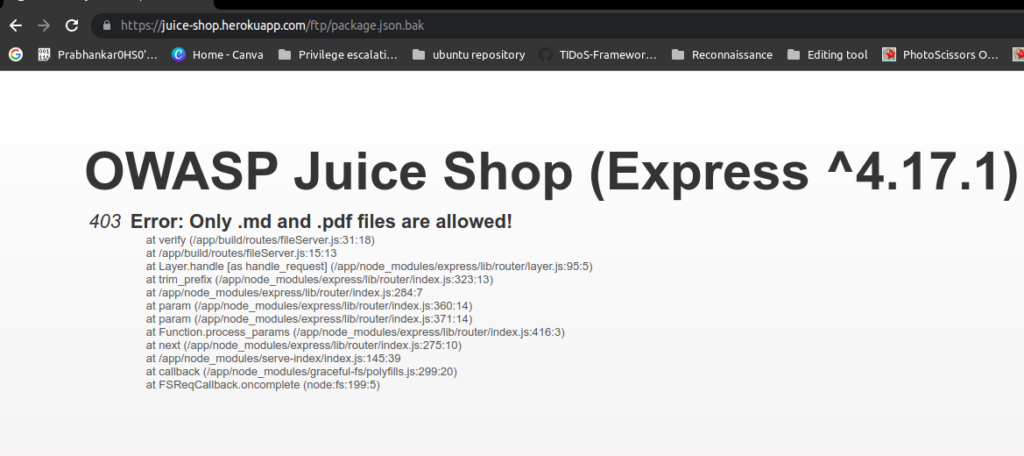
Open the FTP link again https://juice-shop.herokuapp.com/ftp and click on package.json.bak file, it is a backup file we tried to download it but when we click on it it is giving me 403 error only .md and .pdf are allowed
To get around this, we will use a character bypass called “Poison Null Byte“. A Poison Null Byte looks like this: %00. the file name will be package.json.bak%25%30%30.md we encode %00 in url encoding and put it in the end of url.
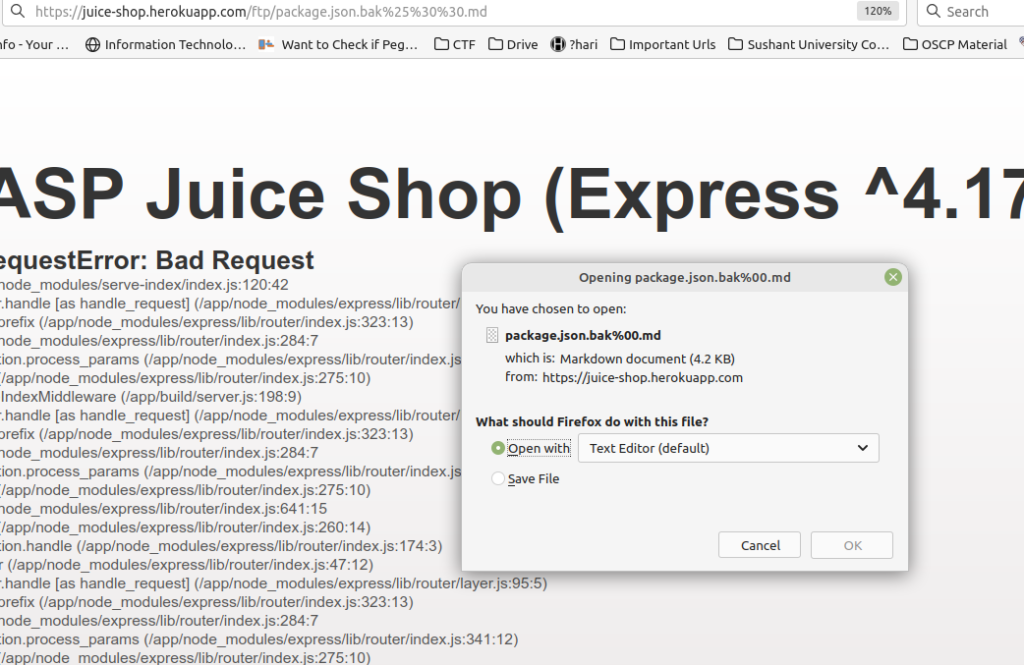
Finally we have downloaded the backup file.
The backup file can contain old and current version of files on the web server. this file could include sensitive data like password, configuration file or even the applications source code. This information could lead to further attack.
Author: Dhakshana E is a passionate Cybersecurity Intern, contact LinkedIn