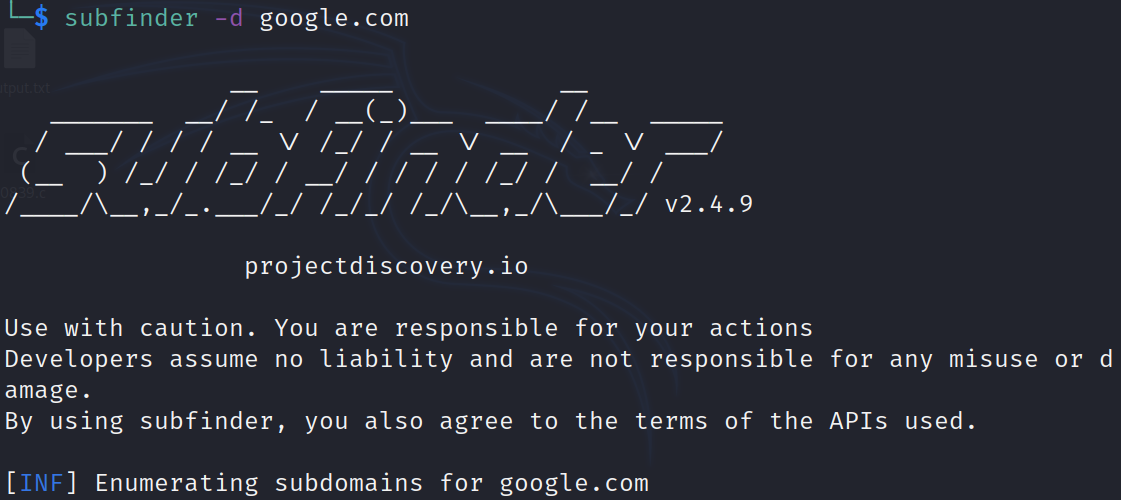
Subfinder: Subdomain enumeration tool Hello Friends, in this blog we are going to learn about the subdomain enumeration tool subfinder…
Tech Blogs
Reconnaissance ctf – tryhackme Hello Friends! I’m going to make a write-up about the secuneus CTF room Task 3 Reconnaissance…
Secuneus CTF SqlI-Tryhackme Hello Friends, I’m going to make a write-up about tryhackme’s room task 6 Secuneus CTF SQLi In…
Owasp Juicy Shop | Sensitive Data Exposure Sensitive Data Exposure: Sensitive Data Exposure vulnerabilities can occur when a web application…
Owasp Juicy shop | Broken Authentication In this blog we are going to learn about the broken authentication vulnerability Owasp…
Injection Vulnerability | Owasp juicy shop Introduction: This is the official companion guide to the OWASP Juice Shop application. Being a web…
Tryhackme Rpmetasploit CTF Hello Friend ! i’m going to make a write-up about tryhackme’s room Metasploit: Exploitation. Metasploit: Metasploit Framework…
Image Source: https://qawerk.com/wp-content/uploads/2021/07/Cover.png Sql Injection PentesterLab In this blog we are going to use PentesterLab vulnerable lab and try to…