SSL Stripping
Introduction
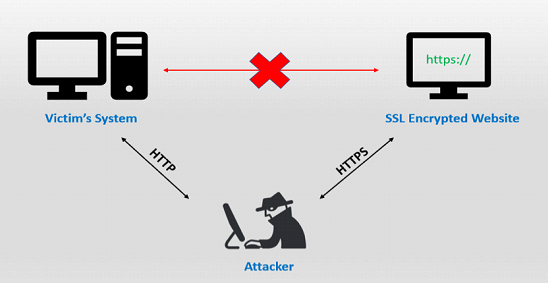
Another form of man-in-the-middle attack happens when a hacker manages to stage an SSL stripping scheme against the victim. In the case of SSL stripping, the attackers downgrade the communications between the client and server into an unencrypted format to be able to stage a MitM attack.
SL stripping is a technique by which a website is downgraded from https to http. In other words, the attack is used to circumvent the security which is enforced by SSL certificates on https sites. This is also known as SSL downgrading. The attacks expose the website to eavesdropping and data manipulation by forcing it to use insecure HTTP rather than secured https. When you enter the URL on the browser, the first connection will be a plain http before it gets redirected to secure https. The attacker takes advantage of this small window by using the SSL strip attack.
Stripping away the encryption offered by HTTPS, called SSL Strip, is a serious cyber threat to many corporations since their employees are constantly on the move and require access to Internet on-the-go even through open non-secure Wi-Fi hotspots. Once attackers gain access to a network, they can act as a Man-in-the-Middle (MITM) to intercept connections over the network. These interception tactics can also be deployed against wired networks, provided that someone gains access to an Ethernet port.
History
The creator of SSL strip vulnerability is Moxie Marlinspike, a well-known American computer security researcher. In 2009, he spoke about this dangerous SSL weakness for the first time at the Black Hat information security event. According to Marlinspike’s presentation, the exploitation of this vulnerability is very serious threat for the privacy of our digital credentials since it can happen in real time, undetected, and targets whatever secure sites people are browsing to at any moment. It doesn’t require multiple certificates and once the attacker gets his “dirty work” done, he can switch the victims back to a normal traffic stream.
Theory
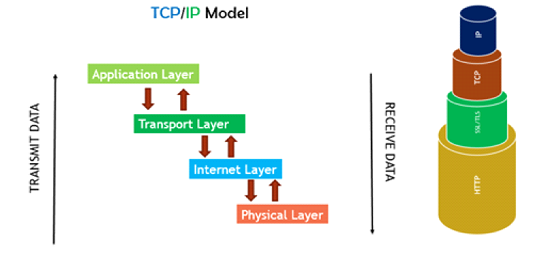
HTTP and HTTPS are the application-layer protocols in a TCP/IP model, as illustrated in the figure below. HTTPS uses a secure tunnel to transfer and receive data which is commonly called SSL/TLS (Secure Socket Layer / Transport Layer Security), and therefore the suffix ‘S’ is added to HTTPS.
Another form of man-in-the-middle attack happens when a hacker manages to stage an SSL stripping scheme against the victim. In the case of SSL stripping, the attackers downgrade the communications between the client and server into an unencrypted format to be able to stage a MitM attack.
SL stripping is a technique by which a website is downgraded from https to http. In other words, the attack is used to circumvent the security which is enforced by SSL certificates on https sites. This is also known as SSL downgrading. The attacks expose the website to eavesdropping and data manipulation by forcing it to use insecure HTTP rather than secured https. When you enter the URL on the browser, the first connection will be a plain http before it gets redirected to secure https. The attacker takes advantage of this small window by using the SSL strip attack.
Stripping away the encryption offered by HTTPS, called SSL Strip, is a serious cyber threat to many corporations since their employees are constantly on the move and require access to Internet on-the-go even through open non-secure Wi-Fi hotspots. Once attackers gain access to a network, they can act as a Man-in-the-Middle (MITM) to intercept connections over the network. These interception tactics can also be deployed against wired networks, provided that someone gains access to an Ethernet port.
History
The creator of SSL strip vulnerability is Moxie Marlinspike, a well-known American computer security researcher. In 2009, he spoke about this dangerous SSL weakness for the first time at the Black Hat information security event. According to Marlinspike’s presentation, the exploitation of this vulnerability is very serious threat for the privacy of our digital credentials since it can happen in real time, undetected, and targets whatever secure sites people are browsing to at any moment. It doesn’t require multiple certificates and once the attacker gets his “dirty work” done, he can switch the victims back to a normal traffic stream.
Theory
HTTP and HTTPS are the application-layer protocols in a TCP/IP model, as illustrated in the figure below. HTTPS uses a secure tunnel to transfer and receive data which is commonly called SSL/TLS (Secure Socket Layer / Transport Layer Security), and therefore the suffix ‘S’ is added to HTTPS.
SSL/TLS is a secure protocol used to communicate sensitive information. This protocol is used when exchanging sensitive data such as banking information and email correspondence for example. The protocol’s security is established by creating an encrypted connection between two parties (usually a client application and a server). Browsers and web servers regularly use this protocol when a secure connection is needed. In most scenarios the following events take place when establishing a secure connection:
⦁ The user sends an unsecured HTTP request.
⦁ The server answers via HTTP and redirects the user to a secure protocol (HTTPS).
⦁ The user sends a secure HTTPS request, and the secure session begins.
This process provides a reasonable guarantee of both privacy and integrity. In other words, we don’t just encrypt the messages we’re sending, we make sure the message we receive isn’t altered over the wire.
Working
In order to “strip” the SSL, an attacker intervenes in the redirection of the HTTP to the secure HTTPS protocol and intercepts a request from the user to the server. The attacker will then continue to establish an HTTPS connection between himself and the server, and an unsecured HTTP connection with the user, acting as a “bridge” between them.
⦁ The user sends an unsecured HTTP request.
⦁ The server answers via HTTP and redirects the user to a secure protocol (HTTPS).
⦁ The user sends a secure HTTPS request, and the secure session begins.
This process provides a reasonable guarantee of both privacy and integrity. In other words, we don’t just encrypt the messages we’re sending, we make sure the message we receive isn’t altered over the wire.
Working
In order to “strip” the SSL, an attacker intervenes in the redirection of the HTTP to the secure HTTPS protocol and intercepts a request from the user to the server. The attacker will then continue to establish an HTTPS connection between himself and the server, and an unsecured HTTP connection with the user, acting as a “bridge” between them.