Introduction
Nikto, also known as Nikto2, is an open source (GPL) and free-to-use web server scanner which performs vulnerability scanning against web servers for multiple items including dangerous files and programs, and checks for outdated versions of web server software. It also checks for server configuration errors and any possible vulnerabilities they might have introduced.
The Nikto vulnerability scanner project is a fast-moving effort, frequently updated with the latest known vulnerabilities. This allows you to scan your web servers with confidence as you search for any possible issues.
Main features
- Nikto is free to use, open source and frequently updated
- Can be used to scan any web server (Apache, Nginx, Lighttpd, Litespeed, etc.)
- Scans against 6,700+ known vulnerabilities and version checks for 1,250+ web servers (and growing)
- Scans for configuration-related issues such as open index directories ● SSL certificate scanning
- Ability to scan multiple ports on a server with multiple web servers running ● Ability to scan through a proxy and with http authentication
- Ability to specify maximum scan time, exclude certain types of scans and unusual report headers seen as well
Nikto installation
The Nikto vulnerability scanner can be installed in multiple ways on both Windows- and Linux-based systems. It is available in package format on Linux for easy installation via a package manager (apt, yum, etc.) and also available via GitHub to be installed or run directly from the project source.
Kali Linux-based installation
Kali Linux is the go-to Linux distribution for users who are into pentesting and security analysis. And adding the Nikto vulnerability scanner to your security analysis tool set on Kali Linux can be achieved with just a couple of commands, as shown below.
First, refresh your APT package lists and install any pending updates:


10 Nikto commands to perform vulnerability scanning
- Running a basic website scan
The most basic way to scan a host with Nikto is to use the -h flag with the nikto command:
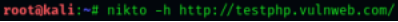
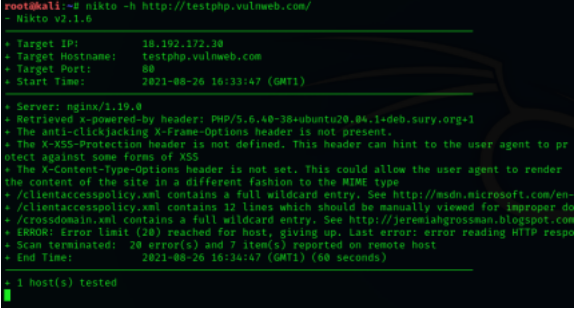
Note: Nikto does a deep scan of the web server, and it may take a long time to finish due to the number of vulnerabilities Nikto checks against. Run under a “screen” session if running Nikto scanner from a remote machine. 2. Running a scan on a website with SSL
Nikto also has an SSL scanner mode, for SSL certificates installed on a website. With this you can get SSL cipher and issuer information. To run a website SSL scan run:

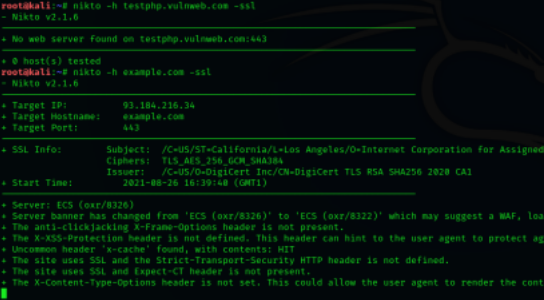
As seen above, when scanning with the -ssl option enabled, we can find more vulnerabilities and configuration errors present in the web server we’ve just scanned when compared to the non-ssl scan. This is often observed with misconfigured web servers, which hastily include SSL support.
- Scanning specific ports with Nikto
On certain deployments, web servers are run on non-standard ports like 8081 or 8080, or multiple web servers are run on the same host on different network ports. It’s therefore vital to have the ability to scan specific ports as well as the main 80 and 443 ports.
This can be achieved by running the command: