GOBUSTER
One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do
this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring. Gobuster is a tool used to brute-force URIs (directories and files) in web sites, DNS subdomains (with wildcard support) and Virtual Host names on target web servers. Traditional directory brute-force scanners like DirBuster and DIRB work just fine, but can
often be slow and prone to errors. Gobuster is a Go implementation of these tools and is offered in a convenient command-line format. The main advantage Gobuster has over other directory scanners is speed. As a programming language, Go is known to be fast. It also has excellent support for concurrency so that Gobuster can take advantage of multiple threads for faster processing.
this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring. Gobuster is a tool used to brute-force URIs (directories and files) in web sites, DNS subdomains (with wildcard support) and Virtual Host names on target web servers. Traditional directory brute-force scanners like DirBuster and DIRB work just fine, but can
often be slow and prone to errors. Gobuster is a Go implementation of these tools and is offered in a convenient command-line format. The main advantage Gobuster has over other directory scanners is speed. As a programming language, Go is known to be fast. It also has excellent support for concurrency so that Gobuster can take advantage of multiple threads for faster processing.
Install Gobuster
Firstly, we need to install Gobuster since it is not included on Kali by default.
Firstly, we need to install Gobuster since it is not included on Kali by default.
Then, simply type gobuster in the terminal to run the tool.

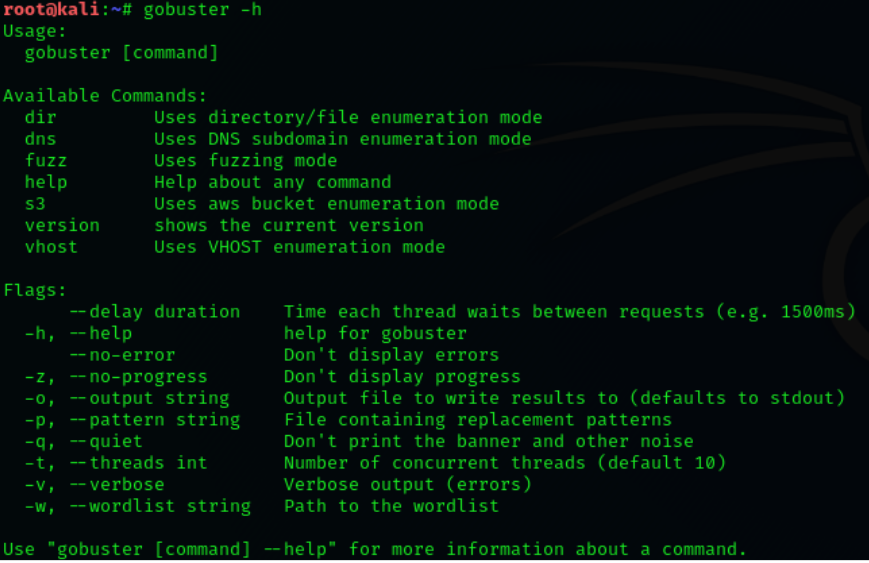
We can also display the help menu with the -h flag.
Installing Additional Seclists for brute-forcing Directories and Files. By default, Wordlists on Kali are located in the /usr/share/wordlists directory.
Or
We can download our suitable wordlist by using following command:
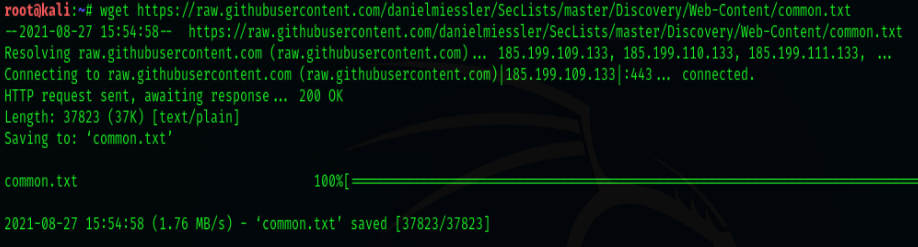
As we can see in the above screenshot our we have downloaded a wordlist named
common.txt and located it in the root folder.
Now everything is ready and we are set for sun Gobuster.
common.txt and located it in the root folder.
Now everything is ready and we are set for sun Gobuster.
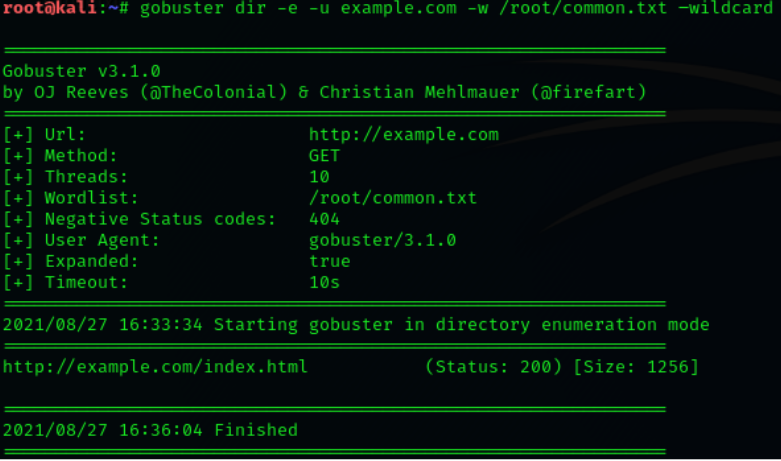
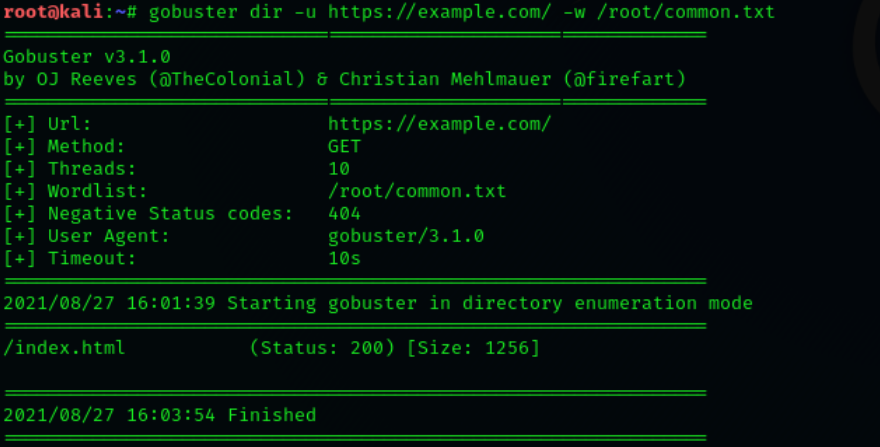
Let it run against our example target with default parameters.
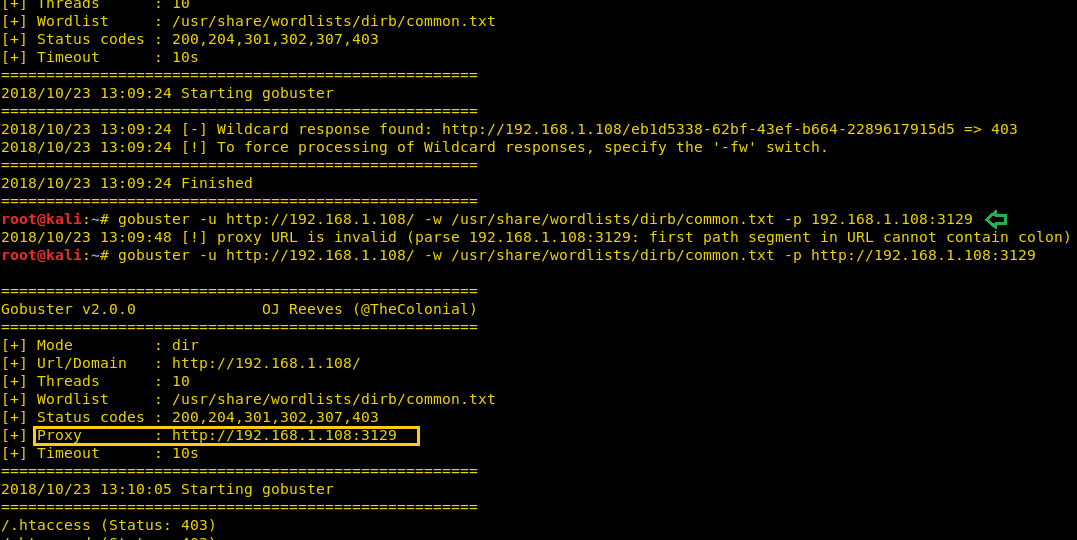
Wordlist Specification
Wordlist Specification
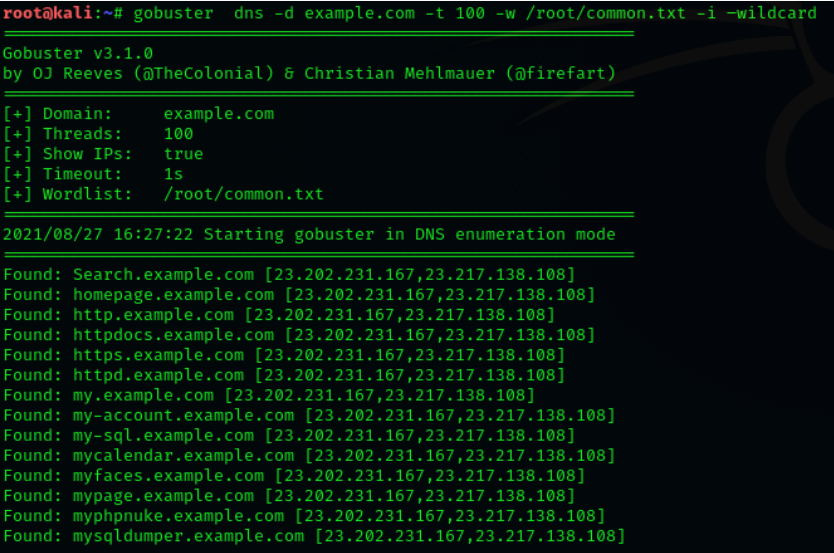
Obtain Sub Domain IPs
Usingthei optionallowstheIPparameter,whichshouldshowtheIPsofselected
sub-domains.
Usingthei optionallowstheIPparameter,whichshouldshowtheIPsofselected
sub-domains.
Set Threads Number
Using the -t option enables the number of thread parameters to be implemented while
brute-forcing sub-domain names or directories.
Using the -t option enables the number of thread parameters to be implemented while
brute-forcing sub-domain names or directories.

Obtaining Full Path for a directory or file
Option “-e” is used for completing the printing URL when extracting any hidden file or
hidden directories..
Option “-e” is used for completing the printing URL when extracting any hidden file or
hidden directories..