
Cross-site Scripting (XSS) happens whenever an application takes untrusted data and sends it to the client (browser) without validation. This allows attackers to execute malicious scripts within the victim’s browser which may end in user sessions hijack, defacing web applications or redirecting the user to malicious web sites.
Types of XSS
Stored XSS – Stored XSS also referred to as persistent XSS occurs when user input is stored on the target server like database/message forum/comment field etc. Then the victim is in a position to retrieve the stored data from the online application.
Reflected XSS – Reflected XSS also referred to as non-persistent XSS occurs when user input is instantly returned by an internet application in a mistake message/search result or the input provided by the user as a part of the request and without permanently storing the user provided data.
DOM Based XSS – DOM Based XSS may be a sort of XSS when the source of the info is within the DOM, the sink is additionally within the DOM, and therefore the data flow never leaves the browser.

Example
This web application uses cat parameter to fetch the data and respond accordingly
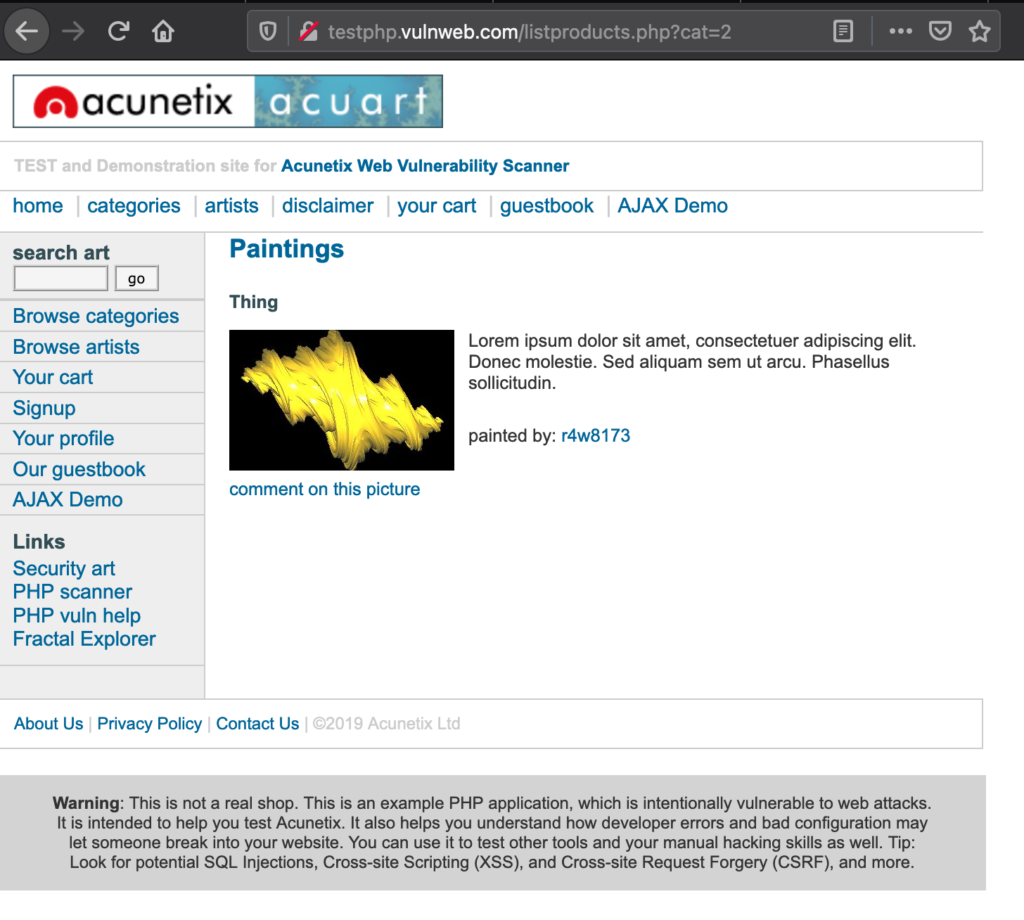
http://testphp.vulnweb.com/listproducts.php?cat=2
The attacker modifies the parameter in the browser to
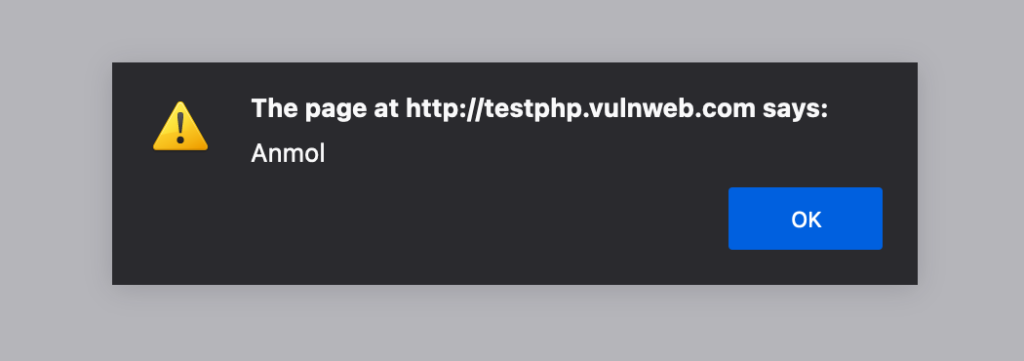
http://testphp.vulnweb.com/listproducts.php?cat=2><script>alert(“Anmol”)</script>
Hands On
Step 1: Let us visit http://testphp.vulnweb.com and navigate to http://testphp.vulnweb.com/listproducts.php?cat=2 Below is the snapshot for the same.
Step 2: Now simply navigate to the browser and modify the URL and add the javascript payload i.e. ><script>alert(“Anmol”)</script> at the end of the URL the modified URL will look similar to this, http://testphp.vulnweb.com/listproducts.php?cat=2><script>alert(“Anmol”)</script>

Step 3: Now all you have to do is hit enter and you will observe a popup that just popped on your browser giving an alert box as can be seen below.
Step 4: This message box is just an example, but the actual attacker can perform much more than just displaying a message box.
XSS Everywhere
Cross Site Scripting attacks were used against British Airways in 2018, stealing private data of 200 million players on an unsecured Fortnite webpage, and in several incidents affecting Twitter and for a massive attack against eBay in 2014. eBay was initially hit by other attacks, leading to user information exposure. Those attacks were followed by a wide exploitation of an XSS vulnerability allowing attackers to steal user details repeatedly. Although being aware of those vulnerabilities, the eBay website has still been reported to suffer from other XSS vulnerabilities recurrently in 2017.
Preventive Mechanisms
- Developers have to ensure that they escape all untrusted data based on the HTML context such as body, attribute, JavaScript, CSS, or URL that the data is placed into.
- For those applications that need special characters as input, there should be robust validation mechanisms in place before accepting them as valid inputs.

