
INTRODUCTION
Wireshark is a free open source tool that analyzes network traffic in real-time for Windows,Mac, Unix, and Linux systems. It captures data packets passing through a network interface(such as Ethernet, LAN, or SDRs) and translates that data into valuable information for IT professionals and cybersecurity teams.
Wireshark is a type of packet sniffer (also known as a network protocol analyzer, protocol analyzer, and network analyzer). Packet sniffers intercept network traffic to understand the
activity being processed and harvest useful insights.
Wireshark (formerly known as ethereal) offers a series of different display filters to transform each captured packet into a readable format. This allows users to identify the
cause of network security issues and even discover potential cybercriminal activity.
Wireshark is absolutely safe to use. Government agencies, corporations, non-profits, and educational institutions use Wireshark for troubleshooting and teaching purposes. There isn’t a better way to learn networking than to look at the traffic under the Wireshark microscope.
How does Wireshark work?
Wireshark is a packet sniffer and analysis tool. It captures network traffic on the localnetwork and stores that data for offline analysis. Wireshark captures network traffic from Ethernet, Bluetooth, Wireless (IEEE.802.11), Token Ring, Frame Relay connections, and more.
Note:
1.A “packet” is a single message from any network protocol (i.e., TCP, DNS, etc.)
2. LAN traffic is in broadcast mode, meaning a single computer with Wireshark can see
traffic between two other computers. If you want to see traffic to an external site, you need to capture the packets on the local computer.
Wireshark allows you to filter the log either before the capture starts or during analysis, so
you can narrow down and zero into what you are looking for in the network trace. For example, you can set a filter to see TCP traffic between two IP addresses. You can set it only to show you the packets sent from one computer. The filters in Wireshark are one of the primary reasons it became the standard tool for packet analysis.
Note:
Wireshark is not an intrusion detection system (IDS). It’s a protocol analyzer, and cannot alert you if someone’s up to no good on your network. What it can do, however, is display malformed packets and visualize traffic – making malicious threats easier to inspect and root out.Wireshark is adept at creating a baseline. With it, you’ll have a far better understanding of what’s normal – and what’s not – for your network.
Wireshark Filters
One of the best features of Wireshark is the Wireshark Capture Filters and Wireshark
Display Filters. Filters allow you to view the capture the way you need to see it so you can troubleshoot the issues at hand. Here are several filters to get you started.
Wireshark Capture Filters:
Capture filters limit the captured packets by the filter. Meaning if the packets don’t match the filter, Wireshark won’t save them.
Here are some examples of capture filters:
host IP-address: this filter limits the capture to traffic to and from the IP address net 192.168.0.0/24: this filter captures all traffic on the subnet. dst host IP-address: capture packets sent to the specified host.
port 53: capture traffic on port 53 only.
port not 53 and not arp: capture all traffic except DNS and ARP traffic.
Wireshark Promiscuous Mode
By default, Wireshark only captures packets going to and from the computer where it runs.
By checking the box to run Wireshark in Promiscuous Mode in the Capture Settings, you can
capture most of the traffic on the LAN, Metrics and statistics,Display Filters and so on.
Wireshark for Windows
You Can Download here :– https://www.wireshark.org/download.html
Wireshark comes in two flavors for Windows, 32 bit and 64 bit. Pick the correct version for
your OS. The current release is 3.2.2 as of this writing. The installation is simple and
shouldn’t cause any issues.
What is Wireshark Used For?
Packet analysis software like Wireshark is used by entities that must remain informed about
the state of security of their network, as such, the software is commonly used by
governments, schools, and technology businesses.
Common Wireshark use cases include:
Identify the cause of a slow internet connection
Investigating lost data packets
Troubleshooting latency issues
Detecting malicious network activity
Identify unauthorized data exfiltration
Analyzing bandwidth usage
Tracing voice over Internet (VoIP) calls over the network
Intercepting Man-in-the-Middle (MITM) attacks
Wireshark makes all of the above use cases possible by rendering and translating traffic into
readable formats – saving users the frustrations of having to translate binary information manually. All of this is done in real-time so that detected issues can be rapidly addressed
before they develop into a service outage, or worse, a data breach.
To use Wireshark correctly, you must be aware of the different proctors being processed at
each OSI layer. This will help you decide which layer should be analyzed for each specific
diagnostic requirement.
Here’s a run-through of the protocols being processed at each OSI layer:
Application (Layer 7) – SMTP, HTTP, FTP, POP3, SNMP
Presentation (Layer 6) – MPEG, ASCH, SSL, TLS
Session Layer (Layer 5) – NetBIOS, SAP
Transports Layer (Layer 4) – TCP, UDP
Network Layer (Layer 3) – IPV5, IPV6, ICMP, IPSEC, ARP, MPLS.
Data Link Layer (Layer 2) – RAPA, PPP, Frame Relay, ATM, Fiber Cable, etc.
Physical Layer (Layer 1) – RS232, 100BaseTX, ISDN, 11.
Analyzing data packets on wireshark:-
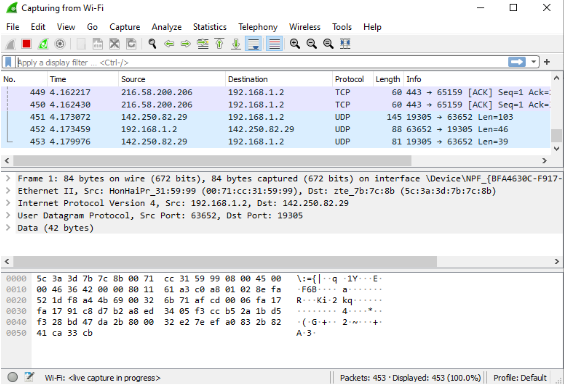
NO : This is the number order of the packet that got captured.
Time: This column shows you how long after you started the capture that this packet
got captured.
Source: This is the address of the system that sent the packet.
Destination: This is the address of the destination of that packet.
Protocol: This is the type of packet, for example, TCP, DNS, DHCPv6, or ARP.
Length: This column shows you the length of the packet in bytes.
Capturing Data Packets on Wireshark
1. When we open Wireshark, we see a screen that shows a list of all of the network connections you can monitor. We also have a capture filter field, so we only capture the network traffic we want to see.
Wireshark is a type of packet sniffer (also known as a network protocol analyzer, protocol analyzer, and network analyzer). Packet sniffers intercept network traffic to understand the
activity being processed and harvest useful insights.
Wireshark (formerly known as ethereal) offers a series of different display filters to transform each captured packet into a readable format. This allows users to identify the
cause of network security issues and even discover potential cybercriminal activity.
Wireshark is absolutely safe to use. Government agencies, corporations, non-profits, and educational institutions use Wireshark for troubleshooting and teaching purposes. There isn’t a better way to learn networking than to look at the traffic under the Wireshark microscope.
How does Wireshark work?
Wireshark is a packet sniffer and analysis tool. It captures network traffic on the localnetwork and stores that data for offline analysis. Wireshark captures network traffic from Ethernet, Bluetooth, Wireless (IEEE.802.11), Token Ring, Frame Relay connections, and more.
Note:
1.A “packet” is a single message from any network protocol (i.e., TCP, DNS, etc.)
2. LAN traffic is in broadcast mode, meaning a single computer with Wireshark can see
traffic between two other computers. If you want to see traffic to an external site, you need to capture the packets on the local computer.
Wireshark allows you to filter the log either before the capture starts or during analysis, so
you can narrow down and zero into what you are looking for in the network trace. For example, you can set a filter to see TCP traffic between two IP addresses. You can set it only to show you the packets sent from one computer. The filters in Wireshark are one of the primary reasons it became the standard tool for packet analysis.
Note:
Wireshark is not an intrusion detection system (IDS). It’s a protocol analyzer, and cannot alert you if someone’s up to no good on your network. What it can do, however, is display malformed packets and visualize traffic – making malicious threats easier to inspect and root out.Wireshark is adept at creating a baseline. With it, you’ll have a far better understanding of what’s normal – and what’s not – for your network.
Wireshark Filters
One of the best features of Wireshark is the Wireshark Capture Filters and Wireshark
Display Filters. Filters allow you to view the capture the way you need to see it so you can troubleshoot the issues at hand. Here are several filters to get you started.
Wireshark Capture Filters:
Capture filters limit the captured packets by the filter. Meaning if the packets don’t match the filter, Wireshark won’t save them.
Here are some examples of capture filters:
host IP-address: this filter limits the capture to traffic to and from the IP address net 192.168.0.0/24: this filter captures all traffic on the subnet. dst host IP-address: capture packets sent to the specified host.
port 53: capture traffic on port 53 only.
port not 53 and not arp: capture all traffic except DNS and ARP traffic.
Wireshark Promiscuous Mode
By default, Wireshark only captures packets going to and from the computer where it runs.
By checking the box to run Wireshark in Promiscuous Mode in the Capture Settings, you can
capture most of the traffic on the LAN, Metrics and statistics,Display Filters and so on.
Wireshark for Windows
You Can Download here :– https://www.wireshark.org/download.html
Wireshark comes in two flavors for Windows, 32 bit and 64 bit. Pick the correct version for
your OS. The current release is 3.2.2 as of this writing. The installation is simple and
shouldn’t cause any issues.
What is Wireshark Used For?
Packet analysis software like Wireshark is used by entities that must remain informed about
the state of security of their network, as such, the software is commonly used by
governments, schools, and technology businesses.
Common Wireshark use cases include:
Identify the cause of a slow internet connection
Investigating lost data packets
Troubleshooting latency issues
Detecting malicious network activity
Identify unauthorized data exfiltration
Analyzing bandwidth usage
Tracing voice over Internet (VoIP) calls over the network
Intercepting Man-in-the-Middle (MITM) attacks
Wireshark makes all of the above use cases possible by rendering and translating traffic into
readable formats – saving users the frustrations of having to translate binary information manually. All of this is done in real-time so that detected issues can be rapidly addressed
before they develop into a service outage, or worse, a data breach.
To use Wireshark correctly, you must be aware of the different proctors being processed at
each OSI layer. This will help you decide which layer should be analyzed for each specific
diagnostic requirement.
Here’s a run-through of the protocols being processed at each OSI layer:
Application (Layer 7) – SMTP, HTTP, FTP, POP3, SNMP
Presentation (Layer 6) – MPEG, ASCH, SSL, TLS
Session Layer (Layer 5) – NetBIOS, SAP
Transports Layer (Layer 4) – TCP, UDP
Network Layer (Layer 3) – IPV5, IPV6, ICMP, IPSEC, ARP, MPLS.
Data Link Layer (Layer 2) – RAPA, PPP, Frame Relay, ATM, Fiber Cable, etc.
Physical Layer (Layer 1) – RS232, 100BaseTX, ISDN, 11.
Analyzing data packets on wireshark:-
NO : This is the number order of the packet that got captured.
Time: This column shows you how long after you started the capture that this packet
got captured.
Source: This is the address of the system that sent the packet.
Destination: This is the address of the destination of that packet.
Protocol: This is the type of packet, for example, TCP, DNS, DHCPv6, or ARP.
Length: This column shows you the length of the packet in bytes.
Capturing Data Packets on Wireshark
1. When we open Wireshark, we see a screen that shows a list of all of the network connections you can monitor. We also have a capture filter field, so we only capture the network traffic we want to see.
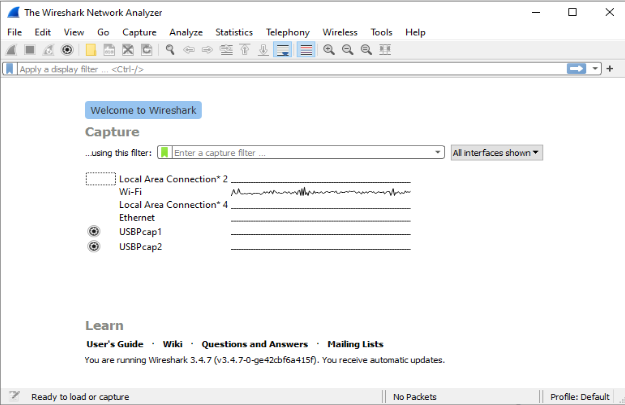
2. we can select one or more of the network interfaces using “shift left-click.” Once we
have the network interface selected, we can start the capture, and there are several
ways to do that.
Click the first button on the toolbar, titled “Start Capturing Packets.”
have the network interface selected, we can start the capture, and there are several
ways to do that.
Click the first button on the toolbar, titled “Start Capturing Packets.”
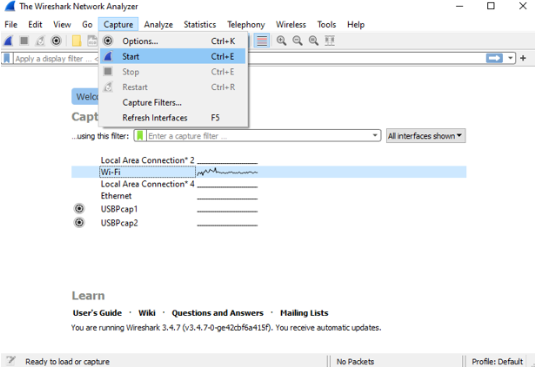
3. We can also select the menu item Capture -> Start Or could use the keystroke Control – E.
4. Then It start capturing the packets. During the capture, Wireshark will show you the packets that it captures in real-time.
5. When all the packets are captured that we need ,then by using the same buttons or menu options we can stop the capture.
Protection against network sniffing:
– Keep antivirus software updated
– Encrypt all network data
– Use a VPN
– Only interact with secure websites
– Do not connect to public Wi-Fi
– Use a third-party attack surface monitoring solution
Protection against network sniffing:
– Keep antivirus software updated
– Encrypt all network data
– Use a VPN
– Only interact with secure websites
– Do not connect to public Wi-Fi
– Use a third-party attack surface monitoring solution

