Introduction
Whenever a request for any website is made from the browser, the browser first resolves the domain name being accessed to an IP address and then sends a request to that address. But what if multiple websites are hosted on the same IP address?
This is where the Host header comes in. This header is used by a web server to decide which website should process the received HTTP request. So whenever multiple websites are hosted on the same IP address, the web server uses the value of this header to forward the HTTP request to the correct website for processing. The purpose of the HTTP Host header is to help identify which back-end component the client wants to communicate with. Several mis configurations and flawed business logic can
expose websites to a variety of attacks via the HTTP Host header. Before diving in, let’s understand some basic terminology.
What is an HTTP Header?
HTTP headers let the client and the server pass additional information with an HTTP request or response. An HTTP header consists of its case-insensitive name followed by a
colon (:), then by its value.
What is a HOST Header?
The Host request header is the mandatory header (as per HTTP/1.1)that specifies the host and port number of the server to which the request is being sent. If no port is included, the default port for the service requested is implied, 443 for an HTTPS URL, and 80 for an HTTP URL.
Example: Host: mysite.net
What is a FORWARDED Header?
The Forwardedheader contains information from the reverse proxy servers that is altered or
lost when a proxy is involved in the path of the request.
The alternative and de-facto standard versions of this header are the X-Forwarded-For,
X-Forwarded-Host and X-Forwarded-Proto headers.
This header is used for debugging, statistics, and generating location-dependent content and
by design, it exposes privacy sensitive information, such as the IP address of the client.
Example: X-Forwarded-For: yoursafesite.net
Reasons leading to Host Header Injection
Any approach in the field of web application if not implemented properly can make room
for several vulnerabilities. Same goes with the implementation of the Host header. If the
application relies on the value of the Host header for writing links without
HTML-encoding, importing scripts, deciding the location to redirect to or even generate
password resets links with its value without proper filtering, validation and sanitization then
it can lead to several vulnerabilities like Cache Poisoning, Cross Site Scripting etc.
Impact: Tampering of Host header can lead to the following attacks
1. Web Cache Poisoning-Manipulating caching systems into storing a page generated with a malicious Host and serving it to others.
2. Password Reset Poisoning-Exploiting password reset emails and tricking them to deliver poisoned content directly to the target.
3. Cross Site Scripting – XSS can be performed, if the value of the Host header is used for writing links without HTML-encoding. For example Joomla used to write Host header to every page without HTML Encoding like this: <link
href=”http://_SERVER[‘HOST’]”> which led to cross site scripting.
4. Access to internal hosts-To access internal hosts.
What is the HOST header attack?
HTTP Host header attacks exploit vulnerable websites that handle the value of the Host header in an unsafe way. If the server implicitly trusts the Host header and fails to validate or escape it properly, an attacker may be able to use this input to inject harmful payloads that manipulate server-side behaviour. What exactly could be the flaw, where it could go wrong? Earlier each IP address would only host content for a single domain. But today, it is common for multiple websites and applications to be accessible under the same IP address. As multiple applications are accessible via the same IP address as regards to — Virtual hosting or Routing traffic via a proxy. It is easy to get lost searching for the origin. Therefore the application relies on the Host header to specify the intended recipient.
Examples:
Web Cache Poisoning using Host Header Injection:
❖Web Cache Poisoning using Single Host Header.
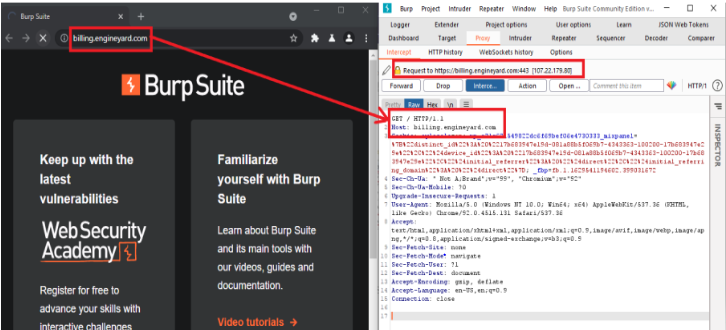
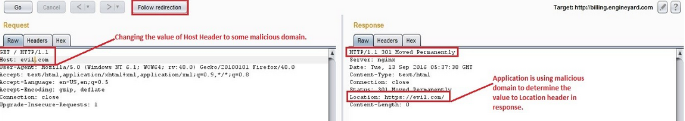
1) Go to the following URL in browser – billing.engineyard.com and intercept the request
using proxy tools such as Burp Suite.
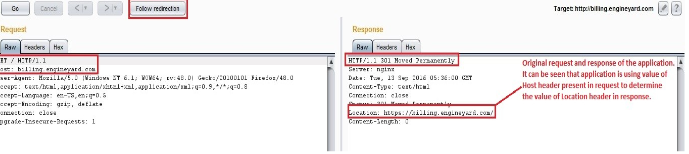
Note: 301 Moved permanently redirects the browser permanently to a different URL, which is specified in the Location header. The client should use the new URL in the future rather than the original.
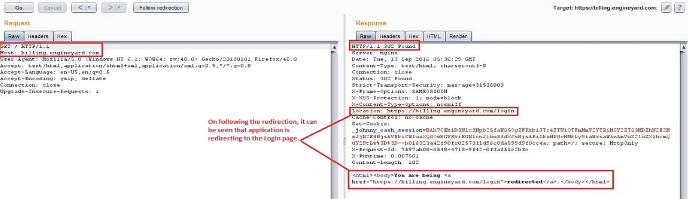
step to some malicious domain and forward it to the server. It may lead to Web Cache
Poisoning as this value is not being validated on the server and the user will be redirected to
http://www.evil.com.
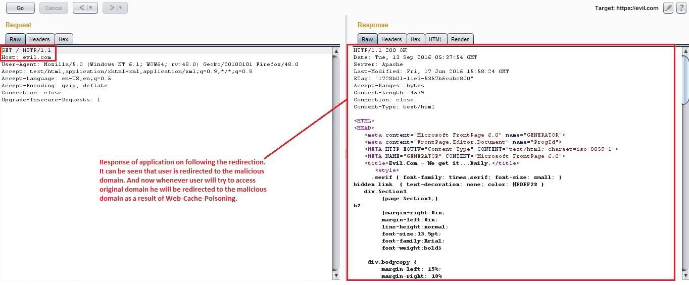
Now whenever a user tries to access billing. engineyard.com from his browser he will be redirected to evil.com since the web-cache has been poisoned as a result of Host header injection.
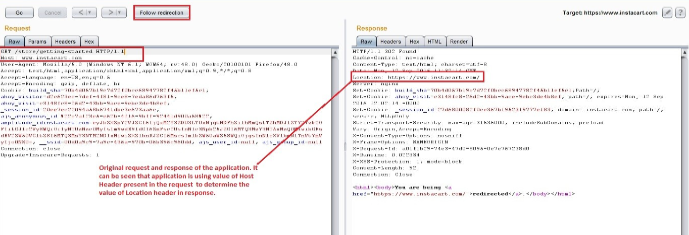
In some cases Host header injection is mitigated by prohibiting tampering of Host header. In that case if any request is made with a tampered host header, the application responds with an error message like “404 Not Found”. There is another way of bypassing arbitrary Host headers by using the X-Forwarded-Host Header. The X-Forwarded-Host HTTP header is used to forward the original Host header value to the origin server. X-Forwarded-Host header is a very crucial HTTP header for determining which Host was originally used when there is a proxy or CDN between the client and origin server. This header is necessary for servers running behind a reverse proxy (such as nginx).
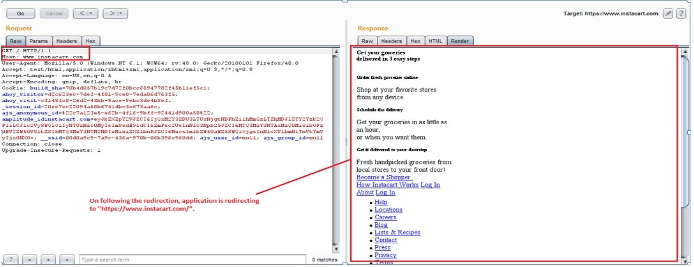
If a request contains the X-Forwarded-Host HTTP header a website would then use its value in place of the actual HTTP hostname. In cases where caching is enabled, this could allow an attacker to potentially embed a remote URL as the base_url for any site. This would then cause other visitors to the site to be redirected unknowingly.Thus if an application fails to prevent a user from using the X-Forwarded-Host header, it will effectively override the Host header.
Example: Steps showing Host Header Injection by using X-Forwarded-Host:
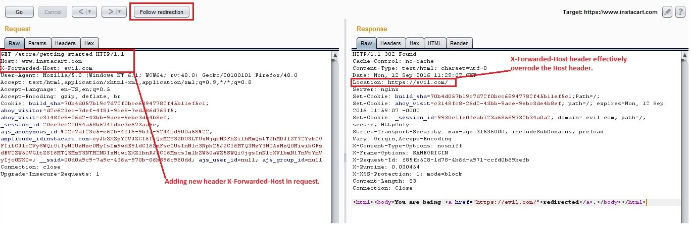
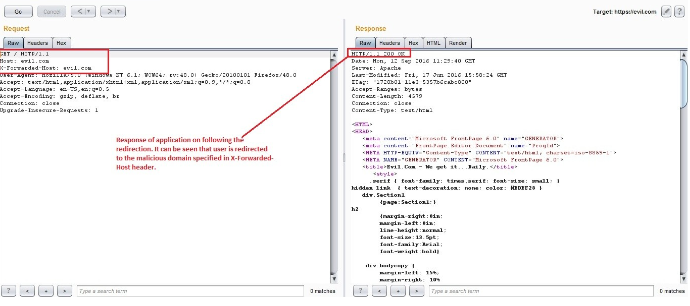
1) Host header injection can be mitigated by rejecting any request that doesn’t match the
target domain.
2) Validating Host header to ensure that the request is originating from that target host or
not.
3) Host header injection can be mitigated in Apache and Nginx by creating a dummy virtual
host that catches all requests with unrecognized Host headers.
4) By creating a whitelist of trusted domains during the initial setup of the application and
mapping domains received in the Host header of each and every request with it.
5) It is recommended to disable the support for the X-Forwarded-Host header and if it can’t
be disabled put proper security checks on it to prevent its tampering.
6) One should use secure server configuration.

