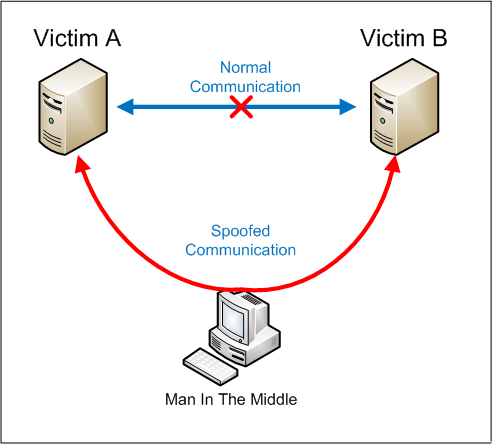
DEFINITION (MITM)
How Man-in-the-Middle Attacks work
Key Concepts of a Man-in-the-Middle Attack
- Are a type of session hijacking
- Involve attackers inserting themselves as relays or proxies in an ongoing, legitimate conversation or data transfer
- Exploit the real-time nature of conversations and data transfers to go undetected
- Allow attackers to intercept confidential data
- Allow attackers to insert malicious data and links in a way indistinguishable from legitimate data
Types of Man-in-the-Middle Attacks
Email Hijacking – attackers gain access to a user’s email account and watch transactions to and from the account. When the time is right, for instance the user is exchanging funds with another party, the attacker takes advantage of the situation by attempting to intercept the funds by spoofing one or all members of the conversation.
Wi-Fi Eavesdropping – a passive way to deploy MITM attacks, Wi-Fi eavesdropping involves cyber hackers setting up public Wi-Fi connections, typically with an unsuspecting name, and gain access to their victims as soon as they connect to the malicious Wi-Fi.
Session Hijacking – session hijacking is when an attacker gains access to an online session via a stolen session key or stolen browser cookies.
DNS Spoofing – an attacker engages in DNS spoofing by altering a website’s address record within a DNS (domain name server) server. A victim unknowingly visits the fake site and the attacker will attempt to steal their information.
IP Spoofing – similar to DNS spoofing, IP Spoofing sees an attacker attempt to divert traffic to a fraudulent website with malicious intent. Instead of spoofing the website’s address record, the attacker disguises an IP (internet protocol) address.
Prevent Man-in-the-Middle Attacks
- Make sure “HTTPS” , with the S – is always in the URL bar of the websites you visit.
- Be wary of potential phishing emails from attackers asking you to update your password or any other login credentials. Instead of clicking on the link provided in the email, manually type the website address into your browser.
- Never connect to public Wi-Fi routers directly, if possible. A VPN encrypts your internet connection on public hotspots to protect the private data you send and receive while using public Wi-Fi, like passwords or credit card information.
- Since MITB attacks primarily use malware for execution, you should install a comprehensive internet security solution, such as Norton Security, on your computer. Always keep the security software up to date.
- Be sure that your home Wi-Fi network is secure. Update all of the default usernames and passwords on your home router and all connected devices to strong, unique passwords.
Implement a comprehensive Email Security Solution – an email security solution is a vital tool in an organizations security architecture that will help minimize the risks associated with MITM. It secures email activity pro-actively while staff focuses efforts elsewhere.
Implement a Web Security Solution – a strong web security tool provides visibility to web traffic generated by both the system and end user at protocol and port layers. Similar to an email security tool, this implementation protects your organization’s web traffic so the security team can cover more ground.
Educate Employees – Making training relevant to the employee is key to training effectiveness. Prepare your workforce for these advanced attacks by educating them on the dynamics, patterns, samples and frequency of attack methods attempted on other organizations. Case studies are a valuable resource when putting together educational materials and awareness programs.
Keep credentials secure – Check your user credentials often. Make sure your passwords are secure, complex and updated every three months at a minimum. This will aid in your company’s protection by keeping credentials fresh and more difficult to crack.



